
In cybersecurity, organizations rely on several tools to assess and improve their security posture: security gap assessments, audits, and risk assessments. While these approaches often overlap in scope, each serves a unique purpose and follows distinct methodologies. Knowing the differences between them isn’t just about semantics. It’s about understanding how to apply these approaches effectively to protect your organization.
For instance, imagine using a gap assessment to pinpoint specific deficiencies in your compliance efforts, an audit to validate that controls are functioning as intended, and a risk assessment to prioritize key investments and map out the bigger picture of threats and vulnerabilities. By knowing when and how to use each, you can strategically prioritize resources, minimize potential risks, and create a more resilient cybersecurity program. Let’s dive deeper into how these approaches differ and how they complement one another.
Security Gap Assessments
A security gap assessment zeroes in on identifying gaps or deficiencies between your organization’s current security measures and a desired state, that should be benchmarked against an industry-recognized standard like the NIST Cybersecurity Framework or ISO 27001 and regulations such as the HIPAA Security Rule. It’s like having a checklist for improvements, pointing out areas where controls are missing, misaligned, or partially implemented. This assessment does not analyze threats, likelihoods, or impacts but emphasizes areas that require enhancement to meet or align with specified controls and requirements.
For example, your assessment might reveal that encryption standards in a cloud environment fall short of ISO 27001 requirements. While valuable for remediation planning, gap assessments stop short of analyzing the broader context, such as how these deficiencies interrelate or interact with potential threats or vulnerabilities.
Audits
Audits are structured, formal reviews aimed at ensuring compliance with specific standards, regulations or internal policy. Think of them as a pass/fail exam, where the focus is on whether controls are properly implemented and functioning as required.
For instance, a SOC 2 audit might evaluate your organization’s controls for security, availability, and confidentiality. Unlike gap assessments, audits are often mandatory for regulatory compliance or client trust. However, they don’t assess external threats, potential vulnerabilities, or the overall risk landscape, leaving key aspects of proactive security management untouched.
Risk Assessments
Risk assessments are the most comprehensive of the three. They go beyond just identifying gaps or verifying compliance but delve into understanding threats, the likelihood of those threats materializing by exploiting a vulnerability or gap, and their potential impact. The insights from a risk assessment allow organizations to prioritize actions that address their most pressing risks.
The result is a comprehensive understanding of overall risk, which supports informed decision-making and prioritization of mitigation strategies. For example, a risk assessment might show that unpatched software carries a low likelihood of issues but poses a high-impact risk because of its critical function in operations. This thorough risk assessment guides the organization in deciding whether to prioritize patching or invest in alternative solutions.
The following highlights the specific assessment tasks found in the methodology from NIST SP 800-30 Guide to Conducting Risk Assessments:
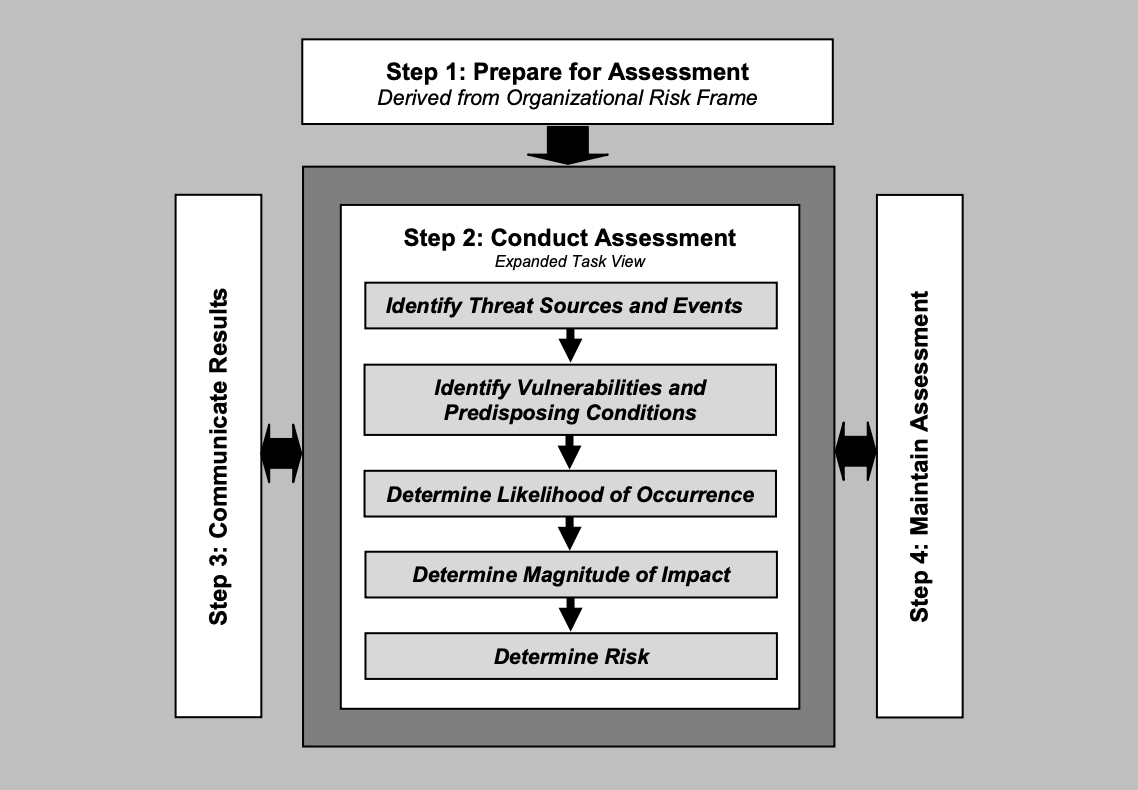
Let’s focus on the primary components of conducting a risk assessment found in Step 2:
- Threat Analysis: Identifying potential threats such as cyberattacks, system failures, or insider misuse.
- Vulnerability Analysis: Examining weaknesses inassets, processes, or controls that could be exploited by threats is essential for understanding the extent of an organization’s exposure.
- Control Analysis: Evaluating how effective existing controls are in mitigatingidentified vulnerabilities and reducing risk exposure.
- Likelihood Determination: Assessing the probability of an undesirable event occurring based on credible threats and an exploitable vulnerability or gap.
- Impact Determination: Evaluating the potential consequencesif a threat were to materialize, including financial, operational, and reputational damage.
- Risk Determination: Combining the likelihood and impact to quantify overall risk levels and prioritize mitigation efforts.
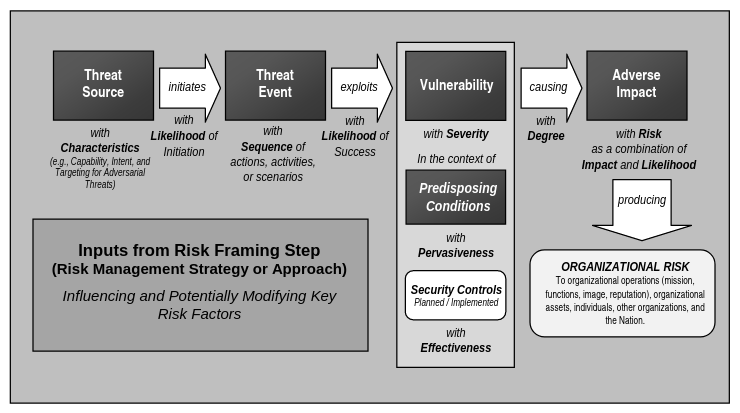
A threat is the acting force that sets an event into motion. To have a threat event, you need to have something of value that can be lost. When a threat causes harm, then you have an adverse impact. A risk determination is the likelihood a threat event will exploit a vulnerability considering the adequacy of security controls and potential adverse impact should the event occur as illustrated in the following risk model:
Case Studies
Risk assessments are a cornerstone of an effective cybersecurity and compliance program, providing organizations with the insights needed to evaluate threats, identify vulnerabilities, and implement appropriate safeguards. However, when organizations neglect or inadequately conduct risk assessments, the consequences can be severe, ranging from data breaches to regulatory fines and reputational damage. Case studies underscore the critical importance of embedding robust risk assessment practices into organizational processes to mitigate threats and ensure adherence to regulatory requirements.
The following real-world examples illustrate how the failure to prioritize thorough and ongoing risk assessments led to significant security incidents and compliance violations:
Equifax
In 2017, Equifax experienced a massive data breach that exposed the personal information of over 147 million individuals. The root cause of the breach was traced to a failure to remediate a known vulnerability in their Apache Struts software. While Equifax had processes in place for vulnerability management, the company did not adequately conduct a thorough risk assessment that would have identified the high likelihood and severe impact of leaving critical systems unpatched. A comprehensive risk assessment would have prioritized patching as a top mitigation strategy, given the sensitivity of the data stored in their systems. This breach underscored the importance of risk assessments and prioritization of mitigation efforts to prevent such catastrophic outcomes.
Citigroup
In 2023, Citigroup was fined $135.6 million by U.S. banking regulators for failing to adequately address long-standing issues in risk control and data management. The Federal Reserve’s review identified ongoing risks, and these penalties highlight the bank’s insufficient risk assessments and failure to implement effective risk management strategies. The lack of comprehensive risk assessments led to substantial financial penalties and reputational damage.
Spanish Data Protection Authority
In 2024, the Spanish Data Protection Authority (AEPD) issued a €6.5 million fine to the telecommunications distributor Phone House Spain SL a following a significant data breach. In April 2021, the company was targeted by a ransomware attack, which encrypted files and interrupted operations. The investigation revealed that the company had not conducted a sufficiently rigorous risk assessment, leading to inadequate preparedness and response to the cyberattack. This case underscores the critical importance of thorough risk assessments in identifying and mitigating potential threats to data.
These examples illustrate the repercussions organizations can face when they neglect to perform comprehensive risk assessments to safeguard against breaches and regulatory penalties.
Regulations and Standards Requiring Risk Assessments
In today’s rapidly evolving cybersecurity landscape, risk assessments play a pivotal role in safeguarding organizational assets and ensuring compliance. Regulatory requirements and security standards worldwide mandate ongoing risk assessments to help organizations identify, evaluate, and mitigate potential threats and vulnerabilities. These assessments not only address compliance requirements but also enable proactive risk management, fostering resilience against evolving cyber threats. From data protection regulations like GDPR to industry-specific standards such as PCI DSS, the emphasis on comprehensive risk assessments underscores their criticality in achieving a secure and compliant operational posture. The following regulations and standards require organizations to conduct risk assessments:
Regulations
- General Data Protection Regulation (GDPR): Article 32 – Requires organizations to regularly evaluate risks to the rights and freedoms of data subjects and mandates implementation of appropriate technical and organizational measures to ensure security, which includes risk assessments to identify potential data vulnerabilities.
- Health Insurance Portability and Accountability Act (HIPAA) – Security Rule – Requires covered entities and business associates to perform regular risk analyses to identify and address potential risks to the confidentiality, integrity, and availability of Protected Health Information (PHI).
- HITRUST – Aligns with HIPAA requirements and mandates risk assessments as part of its control maturity process.
- Digital Operational Resilience Act (DORA) – Requires financial institutions to assess risks to their ICT infrastructure to maintain operational resilience.
- North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) – Mandates risk assessments to protect critical energy infrastructure from cyber threats.
- Sarbanes-Oxley Act (SOX) – Focuses on financial risk, requiring internal controls and risk assessments for financial reporting to ensure the accuracy of corporate disclosures.
- Federal Information Security Management Act (FISMA) – Mandates federal agencies to conduct risk assessments as part of their Information Security Program and implement a framework for identifying and mitigating risks to federal information systems.
Security Standards
- Payment Card Industry Data Security Standard (PCI DSS) – Requires merchants and service providers to conduct periodic risk assessments to identify vulnerabilities and ensure compliance with PCI controls.
- ISO/IEC 27001- Requires organizations to identify and assess risks to information assets as part of an Information Security Management System (ISMS)
- SOC 2 Trust Services Criteria – Requires risk assessments to identify potential threats to the criteria of security, availability, confidentiality, processing integrity, and privacy.
- Critical Security Controls (CIS Controls) – CIS Control 4: Continuous Vulnerability Management emphasizes risk assessments to identify and prioritize remediations.
Why Understanding These Differences Matters
Each method, gap assessment, audit, and risk assessment has its place in an effective cybersecurity program. Gap assessments help you improve; audits keep you compliant; and risk assessments give you the full picture, empowering you to tackle threats head-on through a comprehensive analytical approach.
By conducting an industry-defined risk assessment, organizations can build resilience against threats and vulnerabilities that go beyond compliance checkboxes. This process not only helps identify specific risks but also ensures strategic alignment with business goals, boosting operational continuity, and instilling confidence in stakeholders. By using these three processes together, organizations can ensure they are not only compliant and well-controlled but also more resilient against new threats and vulnerabilities. Recognizing the distinct role of each process helps optimize resource allocation and enhance the overall security posture.
Learn more about Presidio’s Cybersecurity practice here.


