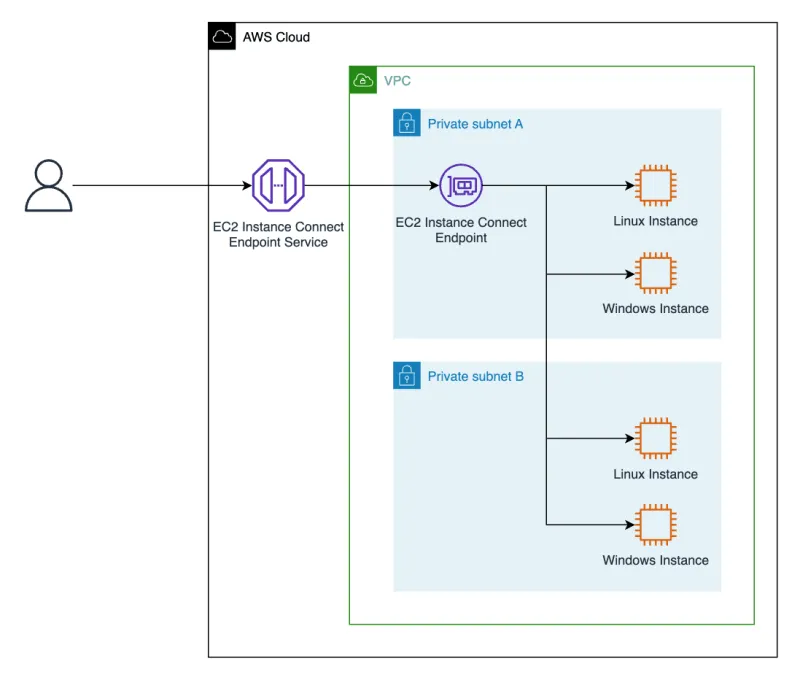
Developers have a common concern with establishing secure internet access to servers within an AWS Virtual Private Cloud (VPC). One commonly used approach is to configure an intermediate bastion in the public subnet to facilitate connections to servers in private subnets.
However, it’s really hard to maintain the ssh keys and the bastion instances for each application or environment, which leads to an operational overhead.
To address these issues, AWS recently announced the EC2 Instance Connect Endpoint service.
What is an instance connect endpoint?
The EC2 Instance Connect Endpoint allows you to connect to an instance without requiring it to have a public IPv4 address. You can connect to any instance that supports TCP.
To connect to an instance, all you need to do is specify the instance ID. You can optionally provide the EC2 Instance Connect Endpoint.
EIC Endpoint eliminates the cost and operational overhead of maintaining bastions. It combines AWS IAM-based access controls to restrict access to trusted principals with network-based controls, such as security group rules, and provides an audit of all connections via AWS CloudTrail, which improves security posture.
Illustration of a user connecting via an EIC Endpoint
IAM Permissions Required To Create EC2 Instance Connect Endpoint
{
"Version": "2012-10-17",
"Statement": [{
"Sid": "GrantAllActionsInAllSubnets",
"Action": [
"ec2:CreateInstanceConnectEndpoint",
"ec2:DeleteInstanceConnectEndpoint",
"ec2:CreateNetworkInterface",
"ec2:CreateTags",
"iam:CreateServiceLinkedRole"
],
"Effect": "Allow",
"Resource": "arn:aws:ec2:region:account-id:subnet/*"
},
{
"Action": [
"ec2:CreateNetworkInterface"
],
"Effect": "Allow",
"Resource": "arn:aws:ec2:::security-group/*"
},
{
"Sid": "DescribeInstanceConnectEndpoints",
"Action": [
"ec2:DescribeInstanceConnectEndpoints"
],
"Effect": "Allow",
"Resource": "*"
}
]
}IAM Permissions Required To Connect Using EC2 Instance Connect Endpoint
{
"Version": "2012-10-17",
"Statement": [{
"Sid": "EC2InstanceConnect",
"Action": "ec2-instance-connect:OpenTunnel",
"Effect": "Allow",
"Resource": "arn:aws:ec2:region:account-id:instance-connect-endpoint/eice-123456789abcdef",
"Condition": {
"NumericEquals": {
"ec2-instance-connect:remotePort": "22"
},
"IpAddress": {
"ec2-instance-connect:privateIpAddress": "10.0.1.0/31"
},
"NumericLessThanEquals": {
"ec2-instance-connect:maxTunnelDuration": "60"
}
}
},
{
"Sid": "Describe",
"Action": [
"ec2:DescribeInstances",
"ec2:DescribeInstanceConnectEndpoints"
],
"Effect": "Allow",
"Resource": "*"
}
]
}Configuring the Security Group
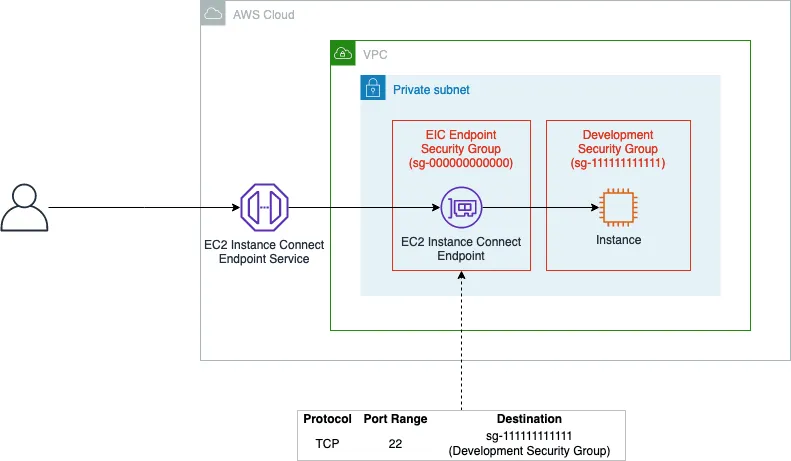
If you don’t specify a security group when creating the EC2 Instance Connect Endpoint, the VPC assigns the default security group. The default outbound rule allows all outbound traffic to reach all destinations. We recommend restricting connectivity to only the instances in the VPC by allowing traffic to the specified destinations.
For the EC2 Instance SG, specify one or more of the following rules, depending on your security needs and whether client IP preservation is enabled:
- Allow inbound traffic from the EC2 Instance Connect Endpoint security group.
- Allow inbound traffic from the client’s IP address.
- Allow inbound traffic from the VPC CIDR so that any instances in the VPC can send traffic to the destination instance.
Creating the Instance Connect Endpoint Using AWS CLI
aws ec2 create-instance-connect-endpoint \
--subnet-id [SUBNET] \
--security-group-id [SG-ID]
Connecting to your Linux Instance using SSH
aws ec2-instance-connect ssh --instance-id [INSTANCE]
Limitations of the ECI Endpoint
- The EC2 Instance Connect Endpoint doesn’t support connections to an instance using IPv6 addresses.
- When client IP preservation is active, the instance to connect to must be in the same VPC as the EC2 Instance Connect Endpoint.
- Traffic routing through an AWS Transit Gateway does not support client IP preservation.
Prerequisites
- You must have the required IAM permission to connect to an EC2 Instance Connect Endpoint.
- To monitor the endpoint state, the EC2 Instance Connect Endpoint must be in the Available (console) or create-complete (AWS CLI) state.
- Make sure you have correctly configured the security group of the instance you want to connect to for inbound traffic.
- When using the AWS CLI, ensure proper configuration and use the latest version.
Reference:
- https://aws.amazon.com/blogs/compute/secure-connectivity-from-public-to-private-introducing-ec2-instance-connect-endpoint-june-13-2023/
- https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/Connect-using-EC2-Instance-Connect-Endpoint.html