
In the rapidly evolving digital landscape, securing cloud environments has become challenging, especially for organizations within the healthcare sector. This case study focuses on a leading provider of healthcare technology solutions, hereafter referred to as ‘the client’.
Enforcing multi-factor authentication (MFA) across their intricate AWS accounts was difficult, emphasizing the complexities of securing sophisticated cloud infrastructures. Presidio’s expertise played a pivotal role in this journey. The process necessitated a deep understanding of the client’s AWS environment and the ability to overcome distinct challenges. We eventually implemented innovative automation solutions that were specifically tailored to meet the client’s needs.
Understanding the client’s AWS environment
The client operates a sophisticated AWS infrastructure, which includes:
- Unique Account Hierarchy: With multiple master payer accounts overseeing a vast network of subsidiary accounts, the client manages a complex ecosystem spanning various business units and operational domains.
- Extensive IAM User Base: Across these accounts, the client maintains a substantial user base, with over 10,000 IAM users requiring secure access to AWS resources.
Challenges and Solutions
Presidio implemented Multi-Factor Authentication (MFA) on the client’s AWS environment to improve security. The key challenges include:
- Fragmented Account Structure: The decentralized nature of the client’s AWS accounts posed a significant challenge in implementing uniform security policies, particularly regarding MFA enforcement.
- Restricted Access for External Consultants: Presidio’s limited access to the client’s AWS environment required innovative approaches to analysis and automation development.
A Strategic Approach to Automation
In pursuit of a fortified security posture, Presidio developed a detailed implementation strategy for MFA enforcement. We centred on creating and attaching IAM policies specifically designed to prevent access to AWS resources without enabling MFA. We formulated these policies to allow users to manage their MFA settings without affecting others, promoting security and individual accountability.
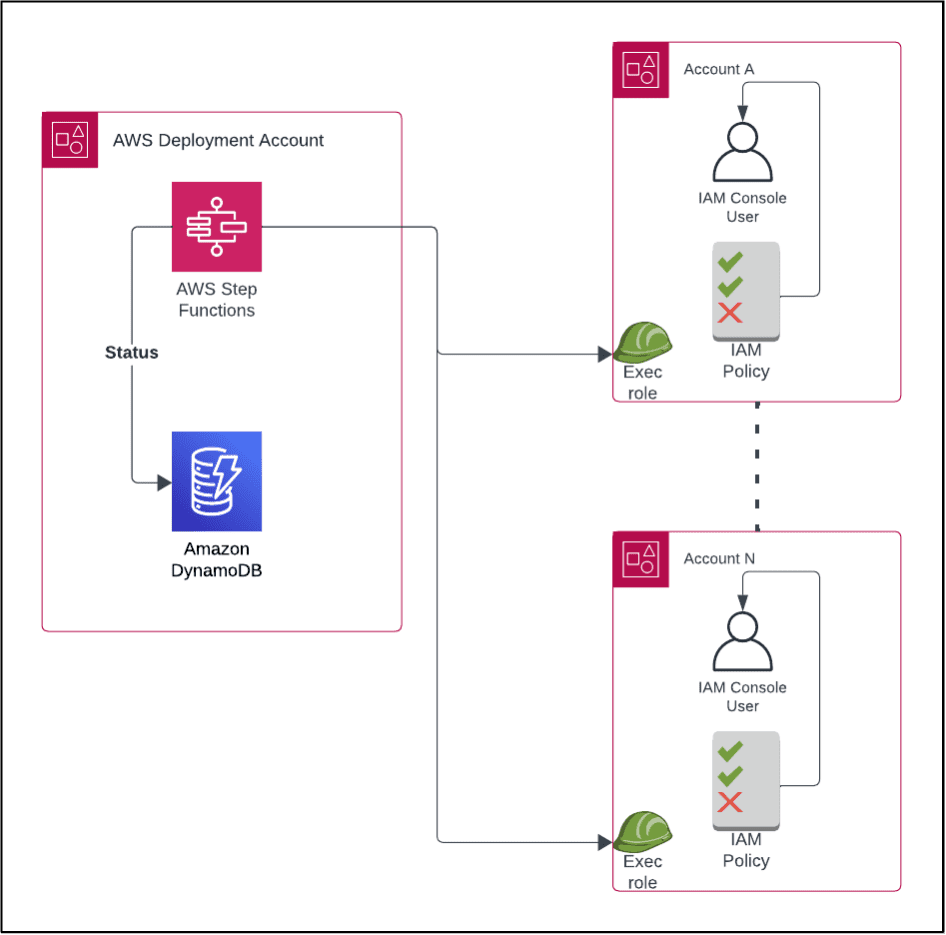
The cornerstone of our implementation was the automated deployment of these policies across the client’s vast AWS account landscape. AWS CloudFormation StackSets enabled scalable and consistent MFA enforcement policies, ensuring that no account was unaffected by our security enhancements.
We managed orchestration, another crucial component, using AWS Step Functions. This setup enabled us to automate the identification of accounts and IAM users, the attachment of MFA enforcement policies, and the meticulous logging of each action for auditing purposes. Such automation not only streamlined the enforcement process but also fortified our compliance and governance framework.
Finally, our strategic use of DynamoDB for logging provided a robust audit trail of enforcement actions. This approach to data management and compliance underscores the rigor and depth of our security strategy.
Enforcement and rollback mechanisms
Presidio designed an intricate system to enforce multi-factor authentication (MFA) across their client’s AWS environment and also ensured they had a clear, structured process for rolling back any changes if needed. This dual approach was critical to maintaining operational flexibility while enhancing security.
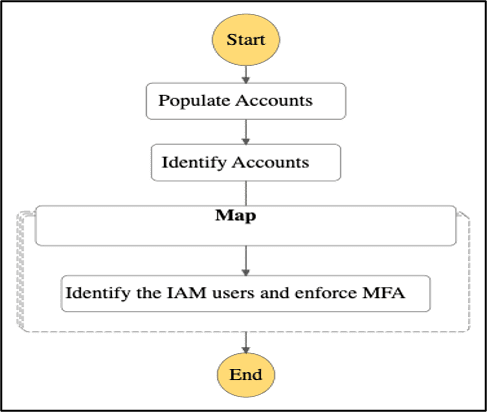
Comprehensive Enforcement through Automation
The cornerstone of our enforcement strategy was the development of customized automation scripts and workflows. We tailored this system to the unique structure of the client’s AWS environment, ensuring it was not a generic solution. We broke down the enforcement process into manageable steps by using AWS Step Functions.
- Policy Deployment: We used automated scripts to create and attach IAM policies that required users to enable MFA. We then attached these policies to all users, but selectively applied enforcement based on their type of access. Specifically, the enforcement targeted users with console access, excluding those who had programmatic access from the MFA requirement.
- Targeted Enforcement: We designed the system to differentiate users based on their MFA status. For users without MFA, the policies restricted access, effectively enforcing compliance. We designed the system to bypass enforcement restrictions for users already in compliance, minimizing disruption to their workflows.
- Audit and Logging: We thoroughly logged every enforcement action in a DynamoDB table. This not only served as an audit trail but also as a valuable resource for reviewing the enforcement process’s effectiveness and identifying any areas for improvement.
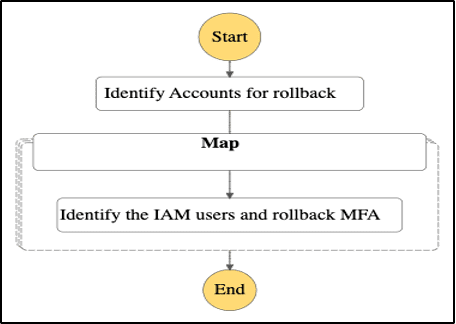
Structured Rollback Procedures for Operational Continuity
To address the need for adaptable security in the client environment, Presidio designed a refined rollback strategy that ensured flexibility and structure. This approach was critical for effectively reversing MFA enforcement actions with minimal disruption to users and operations. The strategy comprised:
- Tailored Rollback Scenarios: Instead of broad triggers, the strategy employed detailed, scenario-specific plans. Each scenario came with a set of predefined actions, targeting only those affected by the enforcement, thereby avoiding unnecessary changes for others.
- Controlled by Step Functions: We executed the rollback through precise JSON inputs using AWS Step Functions, enabling specific, scenario-based actions. This method ensured accuracy and streamlined the rollback process.
- Detailed Audit Trails: Similar to the enforcement phase, we meticulously recorded every rollback, thereby creating a transparent and accountable audit trail. This documentation was crucial for review and upheld high accountability standards.
- Preserving Operational Integrity: The strategy’s core focus was to maintain operational flow and restore user access and settings to their original state. It was vital to ensure business continuity without compromising security or functionality.
Conclusion:
In tackling the client’s complex AWS environment, Presidio demonstrated its deep expertise in cloud security by developing and implementing a tailored multi-factor authentication (MFA) enforcement strategy. Presidio deployed custom IAM policies and strategically used AWS CloudFormation Stack Sets and AWS Step Functions to address the client’s fragmented account structure and the need for precise automation.
This not only ensured a seamless and comprehensive application of MFA across all accounts but also highlighted the ability to maintain operational flexibility and integrity through carefully structured rollback mechanisms. The project exemplifies Presidio’s commitment to delivering sophisticated, client-centric solutions that enhance security without compromising operational efficiency, showcasing our ability to navigate and secure complex cloud environments through strategic planning and advanced technological deployment.










































































































































































































































