Microsoft’s identity platform requires app registration for authentication and authorization. This creates a trust relationship between your app and the platform. Each registration includes certificates and secrets, which serve as passwords for application access. Certificates and secrets often expire unpredictably, requiring regular updates. You can manually manage this for a small number of app registrations, but with 50 to 100 registrations, manual rotation becomes impractical.
To tackle this issue, this blog explores our recent proof-of-concept for automating secret rotation in app registrations. We secure the updated secret by storing it in the respective key vault. The solution leverages Azure’s function app service, using time-triggered functions to periodically check app registrations for expiring secrets. The proposed method integrates a function app into a VNET and uses time-triggered functions based on cron jobs to systematically rotate app registration secrets before they expire, within a 2-day threshold.
We have categorized the concept into four primary divisions, focusing on the most commonly used services for improved comprehension.
- Azure Function App
- App registrations and key vaults
- Networking
- Application Insights
We’ll delve into the application and functionality of each concept, accompanied by prerequisites for the proposed solution and a screenshot. This includes high-level and low-level visual representations.
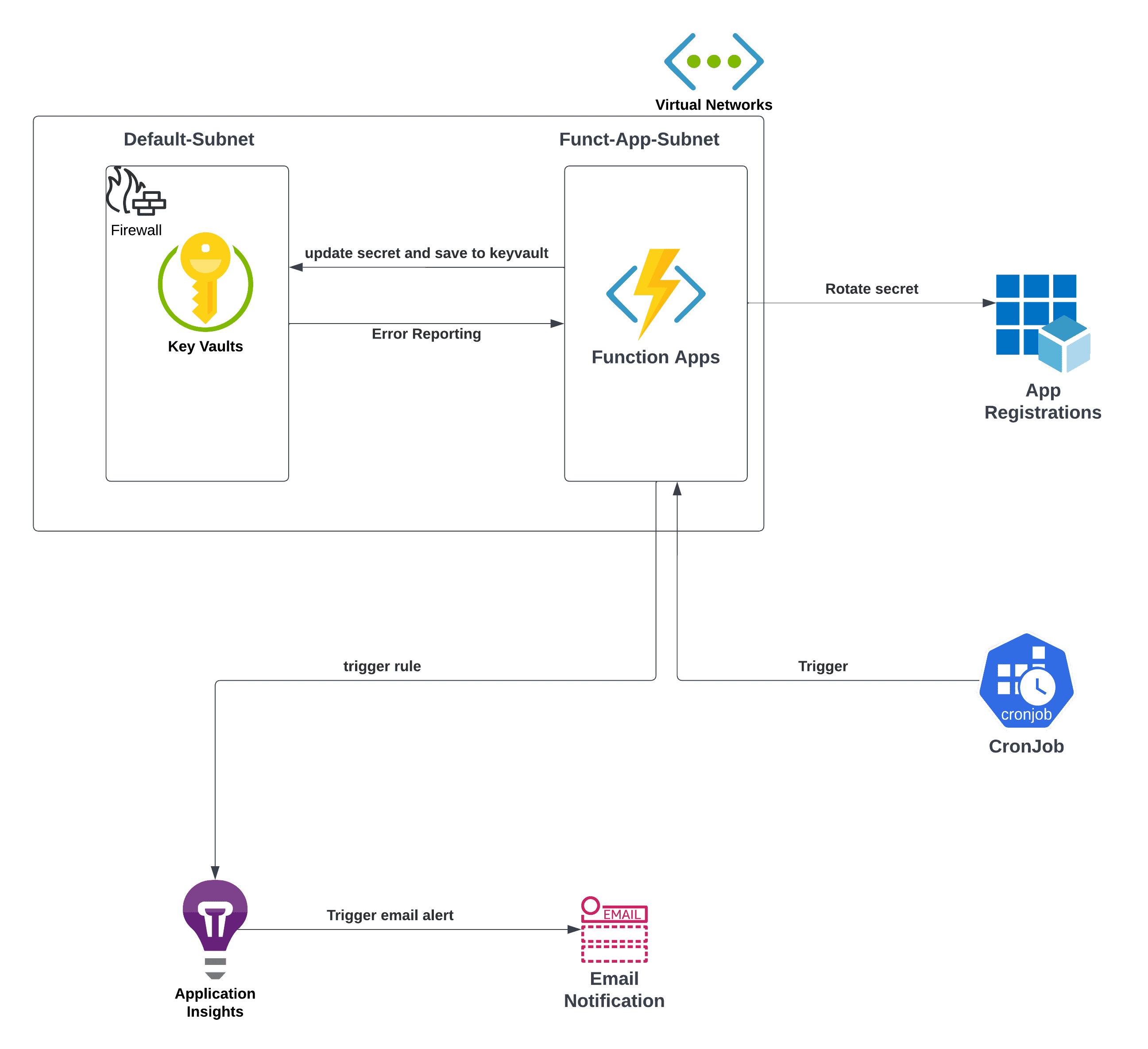
High Level Diagram
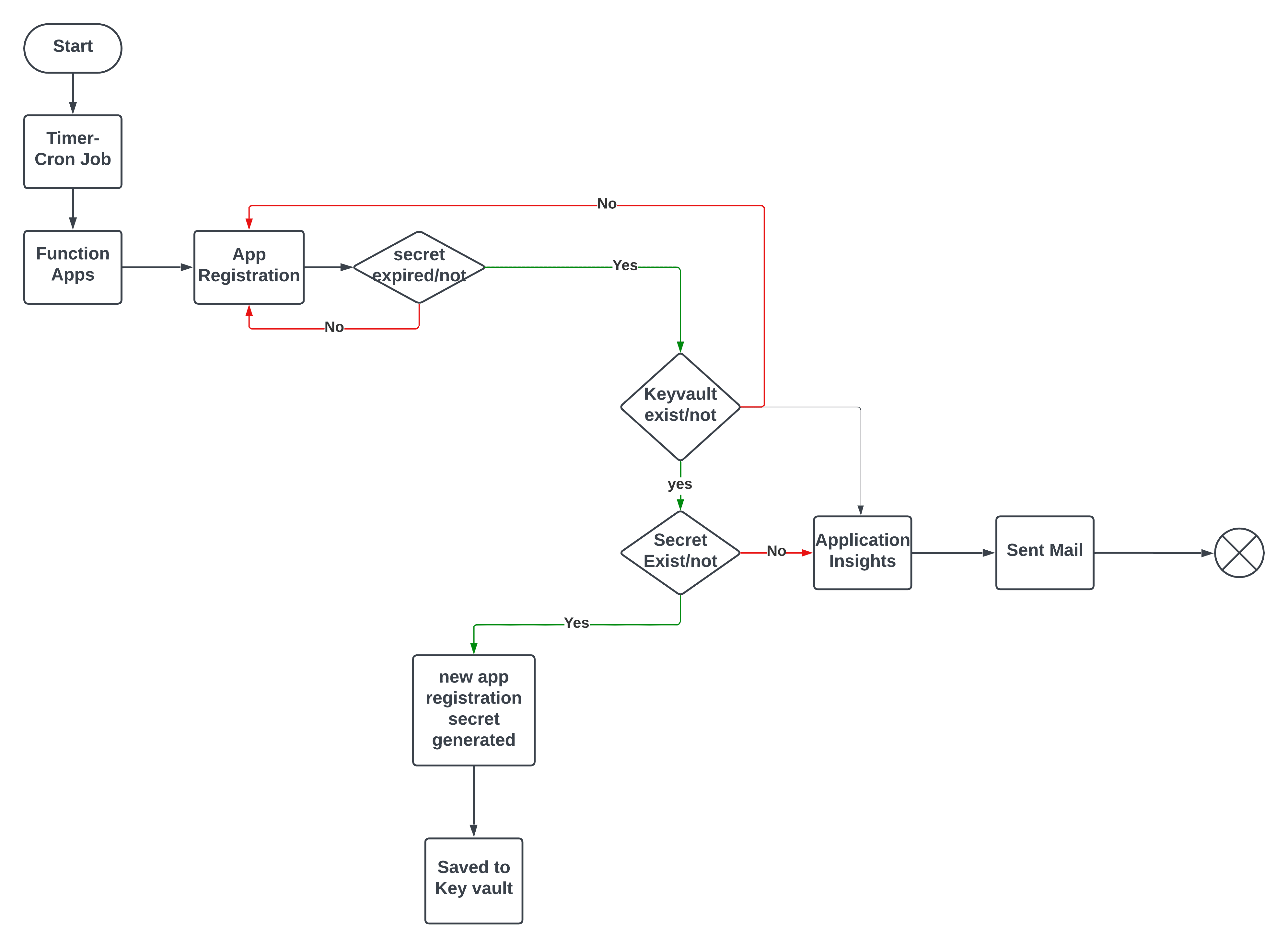
Low level (flow chart) Diagram
Azure Services
Function app:
Time triggered Functions:
Azure’s function app, a serverless solution, minimizes code, infrastructure, and costs. We utilized a timer-triggered function that works on a cron schedule, checking each app registration for expiration. If nearing expiration, the function rotates the secret, storing the new one in the key vault with a tag value as the secret ID.
Role assignments:
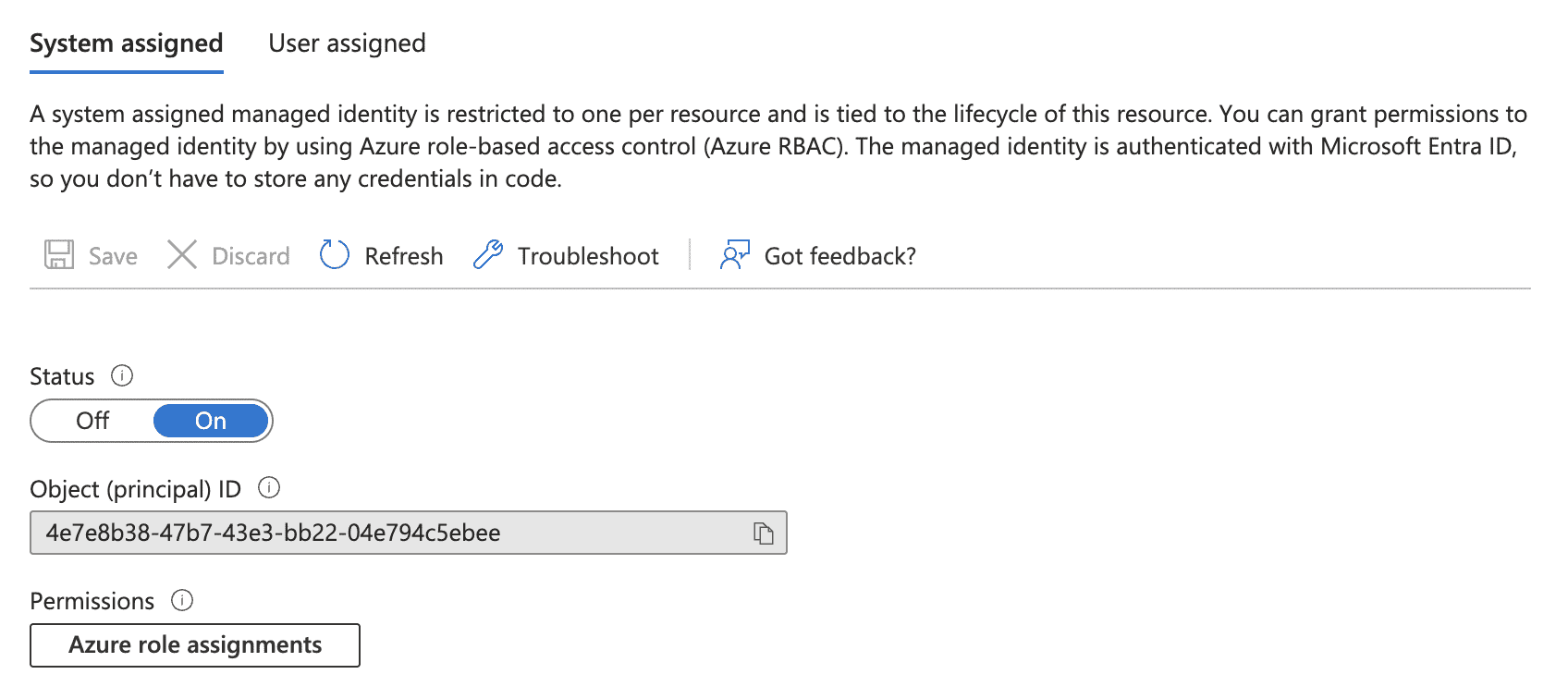
The function application will have a system-assigned identity and RBAC roles. You can use this managed identity to authenticate and authorize the application’s interactions with other Azure services and resources. After granting a system-assigned identity to a function app, you can grant resource-level permissions specific to that identity using Azure RBAC.
Code flow:
The function app examines each app registration’s secrets, checking for expiration of app secrets within a threshold mentioned in the script. If it has expired, it checks the corresponding key vault, which contains the expired app reg secret. You can use the key vault for multiple subscriptions. The function app searches each subscription for the key vault, which contains a newly rotated app secret. This rotation is based on tag values, which include the APP_ID from the respective app registration.
If a secret doesn’t expire, the script prints the message “App secret is not expiring” and proceeds. If the function app doesn’t find a key vault, it sends an informative email to the relevant distribution list (DL) before proceeding to the next app registration secret. The app registration rotates the secret, updates the key vault, and replaces the expired secret if it detects a corresponding key vault and secret. It removes the old expiring app secret. The application insights, integrated with the function app, will trigger an alert rule when a flow error occurs, sending an email to the designated DL in the action group.
Networking
Function app:
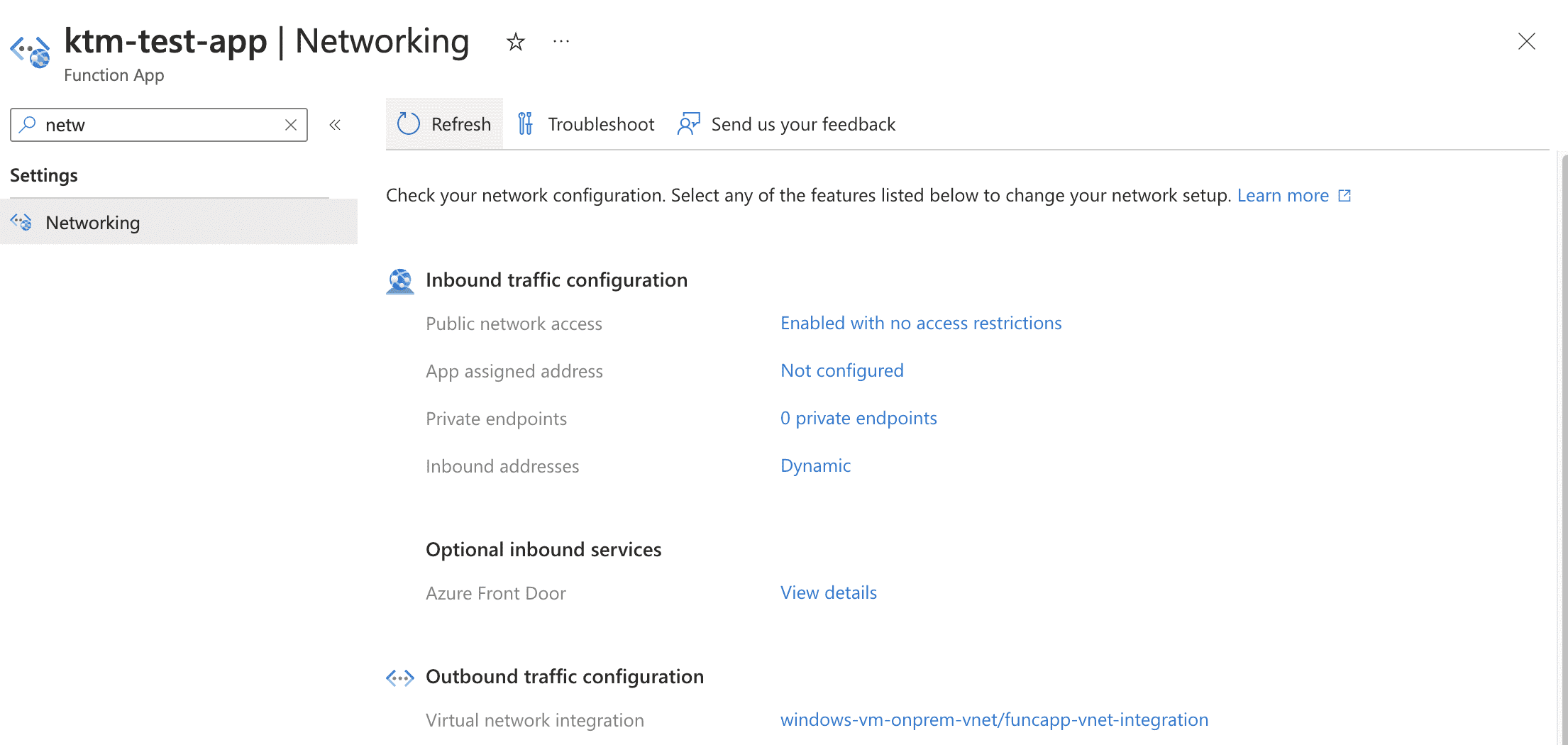
- The function app links to a Virtual Network (VNet) through a private endpoint to manage function app traffic and improve security.
Key vault:
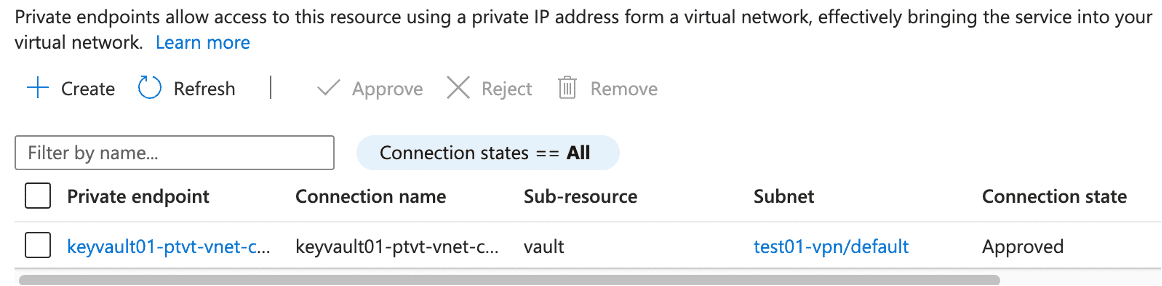
- In our POC, we integrated our Function App and Azure Key Vault into a dedicated Virtual Network. This integration not only ensures secure communication and access control between our Function App and Key Vault, but it also establishes a robust network environment that enhances our applications’ overall security posture by leveraging the benefits of network isolation and private link integration.
Prerequisite:
Adding Tags:
- The tags serve as an identifier for associating the key vault with a particular app registration.
- The app registration’s object ID serves as the tag value, uniquely identifying the app’s associated key vault.
- Once you locate the key vault, you can identify the secret using the associated tag value, which corresponds the secret ID of each app registration secret.
Networking- Checkpoints:
- To ensure integration between the VNet and the function app, it’s crucial to deploy the function app in the same region as the VNet.
- Ensure the VNet has sufficient subnets, including a dedicated empty subnet for the function app.
- A private endpoint connects the key vault and VNet, restricting the key vault’s inbound traffic exclusively to that specific VNet.
Costing:
APP Service Plan:
- Please refer to the official Microsoft documentation for app service plan prices. For our function app, we shared the Premium P2V2 plan, which already exists in our project.
The application insights cost for POC:
Application Insights:
For live web applications, Azure Monitor Application Insights, a feature of Azure Monitor, excels in Application Performance Management (APM). Function apps integrate with application insights to enhance their monitoring.
Alert Rule:
There were two types of alert rules used in our POC:
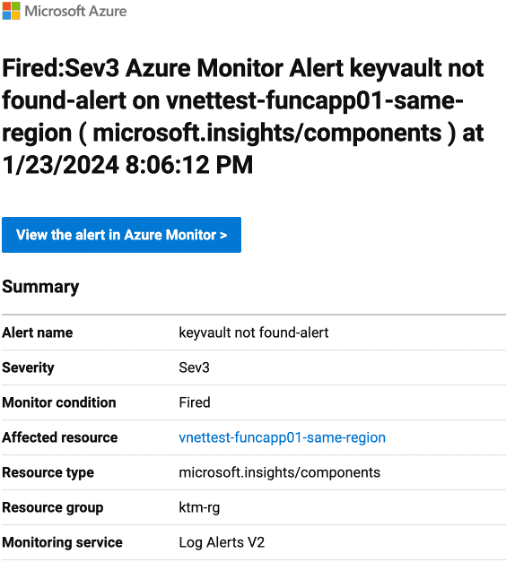
Custom log search: “Key vault not found alert”: This is an informational alert rule. You can use this to send an email if you can’t find the key vault.
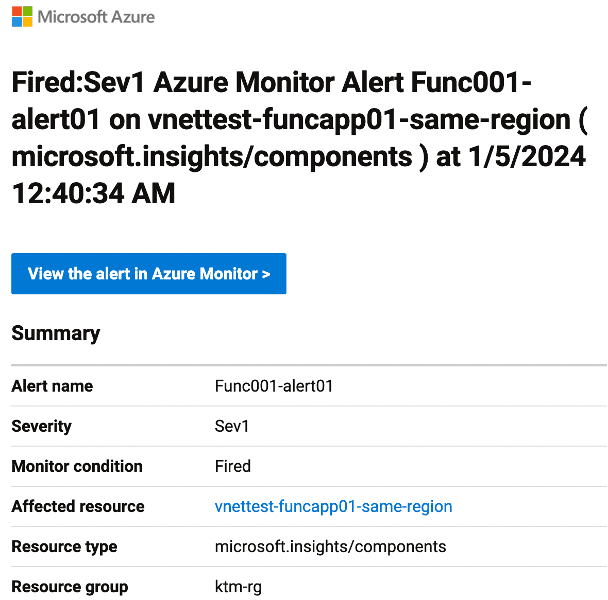
Exceptions – We use this alert to track the execution of the function application. If an error occurs, we will trigger this alert and send an error email.
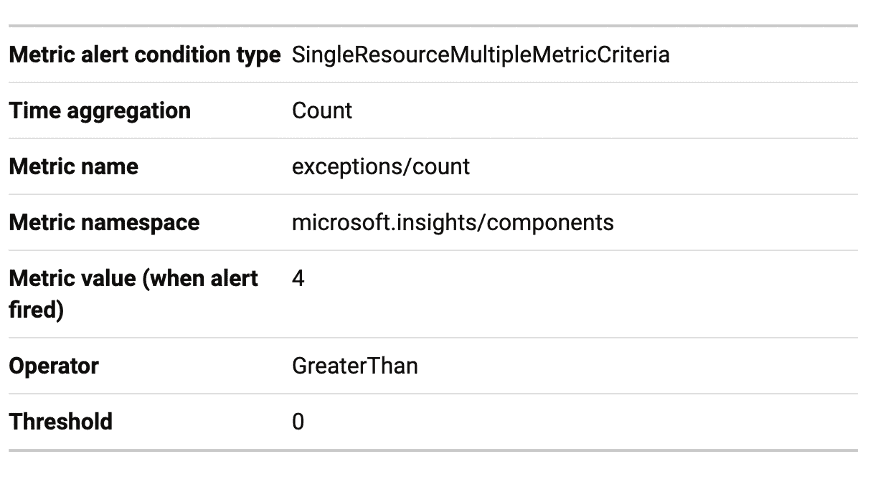
Action Group: The Action Group establishes the Distribution List’s (DL) mail ID for sending alert emails, and then they will notify the concerned person whose mail ID it adds via mail.
Conclusion:
The proposed solution mitigates human errors and reduces time consumption. Over time, the suggested approach will streamline the complexity arising from multiple expiring secrets in app registrations. The alert mail is a valuable monitoring tool because it promptly notifies the issue as soon as it occurs.