
Security is in the news constantly these days with all the bad actors constantly attacking and looking for weaknesses. Knowing this, there is a movement among organizations to not only fortify their perimeters but also incorporate processes that will make their code more secure.
Numerous companies have a team in their firms who have created a codebase that is not optimally managed, much less gone through the necessary security checks. They are looking for help to jump start this process in an optimized manner, utilizing the best tools and practices that other industry leaders have shown as successful in the past. This is where Presidio’s “out of the box” Security based CI/CD pipeline comes in from the DevOps tea. With a time boxed engagement along with pre-built scaffolding, this solution allows for the company to get their build system up and running along with a defined set of customizations that would best meet their needs.
The solution is presented in a ‘good’, ‘better’, and ‘best’ option set, allowing you to select the options that best fit your need. The good foundational solution starts with a CI/CD pipeline that allows your team to start and have a set of security tests right out of the box. The better implementation adds Amazon Workspaces to allow for a development work environment that is controlled and protected. As the best option, a managed Identity provider, like Okta, is added to the environment so that access control can be easily maintained from the corporate environment.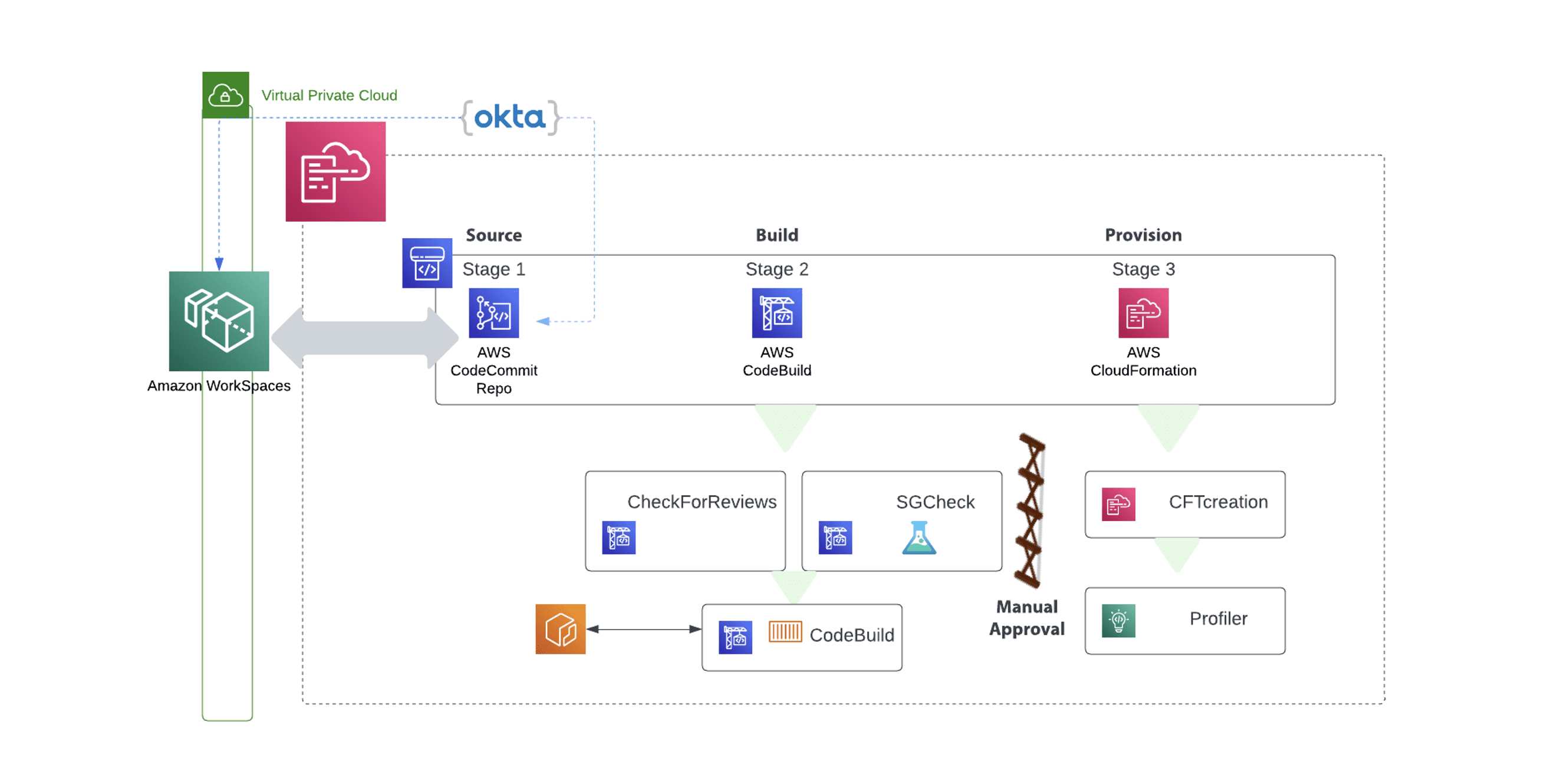
Stages of the process
Once implemented, the newly created pipeline creates three distinct stages that have steps under each stage. The first stage is the Source stage where the CodeCommit repository is tied into the pipeline. The source stage is crucial for the automated kickoff of the pipeline once a new commit has been merged into the main branch.
After the source code has been successfully downloaded and created as an artifact for use throughout the duration of the pipeline, then we move on to the second stage – Build. The Build stage comprises of three separate steps that initially check to see if there were any items found in a previous review performed by AWS CodeGuru Review. If a previous check is found then a message is sent back to the user or distribution list via who is subscribed to the SNS topic.
The final stage of the Build phase is the CodeBuild phase. This is the step where the Dockerfile is used to create the container with code stored and pulled from the CodeCommit repo.
After the Build stage has complete successfully then a manual gate is presented forcing an authorized user to validate and authorize the continuation onto the next step, the Provision phase. There are two steps which compose the Provision Phase. The first is to deploy a CloudFormation Template so that the resources in the code can be spun up for DAST testing. The second is to run the set of SAST tests performed by the AI-based service CodeGuru.
Once CodeGuru has reviewed the code base, then any security issues can be addressed and remediated before deploying the code base into any further upper environments.
Customizations
The Presidio team can help customize your build process by adding items to the engagement such as:
- Pre and post commit hooks for your code versioning system
- Pre-screened software on the Amazon Workspaces
- Creation of IAM groups that map to the Okta user directory with the corresponding permission sets.
Starting the Modernization Process
If you are in the process of modernizing your current set of applications either in preparation or moving them to the AWS Cloud, then you can appreciate the order that an automated pipeline brings to that process. It does not matter the size of the organization, having the key components of code versioning, code checks, and static application security testing (SAST) can help find the security flaws in your codebase. Once these flaws are found then a notification is sent and the pipeline is stopped. A notification is sent out and the development team can then make the adjustments needed and then resubmit and let the pipeline run again.
Protecting your Intellectual Property
With many organizations allowing their employees to Bring Their Own Devices and even more allowing employees to work from home, making sure that you protect the Intellectual Capital that these employees are creating is imperative.
With the ‘better’ option that Presidio offers with this solution, AWS Workspaces is used to create an environment where the code can be created and shared among other team member, but it could never be downloaded or sent out of the working environment.
An overview of the AWS services used in the solution
The example solution employs the following AWS services:
- AWS CodeCommit: a fully managed source control service to host secure and highly scalable private Git repositories.
- AWS CodePipeline: A fully managed continuous delivery service that helps automate release pipelines for fast and reliable application and infrastructure updates
- AWS CodeBuild: A fully managed build service that compiles source code, runs tests, and produces source code and software artifacts.
- AWS CodeDeploy: A building block service that helps automate the deployment and updates of software on any instance, including Lambda functions, both in the AWS cloud and instances running on-premises.
- Amazon CodeGuru: A developer tool providing intelligent recommendations to improve code quality and statically analyze code to look for security issues in five (5) key areas.
- Amazon WorkSpaces: A managed, secure cloud desktop service that allows organizations to provision a needed and restrict access based on Identity and Access Management.
Presidio is an AWS Premier Partner that holds numerous competencies such as the Migration Consulting competency, the DevOps Consulting Competency, the Security Consulting Competency, and the Network Consulting Competency. They have been a part of over 500 AWS customer launches and their team members hold over 500 AWS certifications.










































































































































































































































