
Introduction
In today’s fast-paced software development landscape, ensuring code quality and security is critical. A poorly structured or vulnerable code can lead to technical debt, security risks, and maintainability challenges, ultimately impacting software reliability and business performance. Code analysis plays a vital role in identifying potential bugs, security vulnerabilities, and code smells early in the development lifecycle, enabling teams to enforce coding standards, improve maintainability, and enhance overall software quality.
To strengthen our development pipeline, we conducted a Proof of Concept (POC) for deploying SonarQube Community Edition using Docker with HTTPS on an Ubuntu environment. SonarQube is a widely adopted static code analysis tool that helps teams detect and resolve issues efficiently by providing in-depth insights into code quality, security vulnerabilities, and technical debt.
Why SonarQube with Docker and HTTPS? Why SonarQube?
Frequent code changes and rapid releases in modern agile development environments make it challenging to maintain code quality and security. Manual code reviews alone are not sufficient to detect deeper issues such as security vulnerabilities, code smells, or performance bottlenecks. This is where SonarQube becomes a crucial tool in the development workflow.
SonarQube is a widely adopted static code analysis platform that helps teams enforce best coding practices, identify security flaws, and measure technical debt. It provides comprehensive analysis across multiple programming languages, helping developers to:
- Identify bugs and vulnerabilities early: SonarQube scans the codebase for potential security threats, logic flaws, and bad coding patterns before they reach production.
- Ensure compliance with coding standards: By integrating predefined quality gates and industry-standard rules (e.g., OWASP, SANS Top 25), teams can enforce uniform coding standards across projects.
- Support multiple programming languages: SonarQube works seamlessly with various languages, making it ideal for polyglot development environments where teams use multiple tech stacks.
- Provide actionable insights: Developers get real-time feedback, allowing them to fix issues proactively rather than addressing them post-deployment.
- Integrate smoothly with CI/CD pipelines: SonarQube easily integrates with popular DevOps tools like Jenkins, GitHub Actions, GitLab CI/CD, and Azure DevOps, enabling automated code analysis as part of the software delivery lifecycle.
Why Docker?
Traditionally, deploying SonarQube required manual setup and configuration on a dedicated server, involving dependency management, system compatibility checks, and resource allocation. However, with the need for scalability, consistency, and efficiency, we opted for Docker-based deployment instead of a traditional installation.
By containerizing SonarQube, we gained several key benefits:
- Simplified Deployment & Maintenance: Docker provides a lightweight and consistent way to package and deploy SonarQube without worrying about underlying OS configurations. The entire setup can be spun up quickly with minimal manual intervention.
- Environment Consistency: With Docker, we ensure that SonarQube runs identically across different environments (development, staging, and production), eliminating inconsistencies caused by system dependencies.
- Scalability & Portability: Containers allow us to scale SonarQube efficiently and move workloads across different infrastructures (local, cloud, or hybrid setups) with ease.
- Resource Isolation & Security: Running SonarQube in a containerized environment prevents conflicts with other applications and improves overall security by isolating dependencies.
Advantages of Using AWS Application Load Balancer (ALB) for HTTPS
Rather than configuring HTTPS inside SonarQube or using a reverse proxy like Nginx, we used AWS ALB, which provided:
- Built-in SSL termination—no need for complex certificate management on the instance
- Scalability – ALB distributes requests efficiently.
- Simplified security—integrated with AWS IAM and security groups
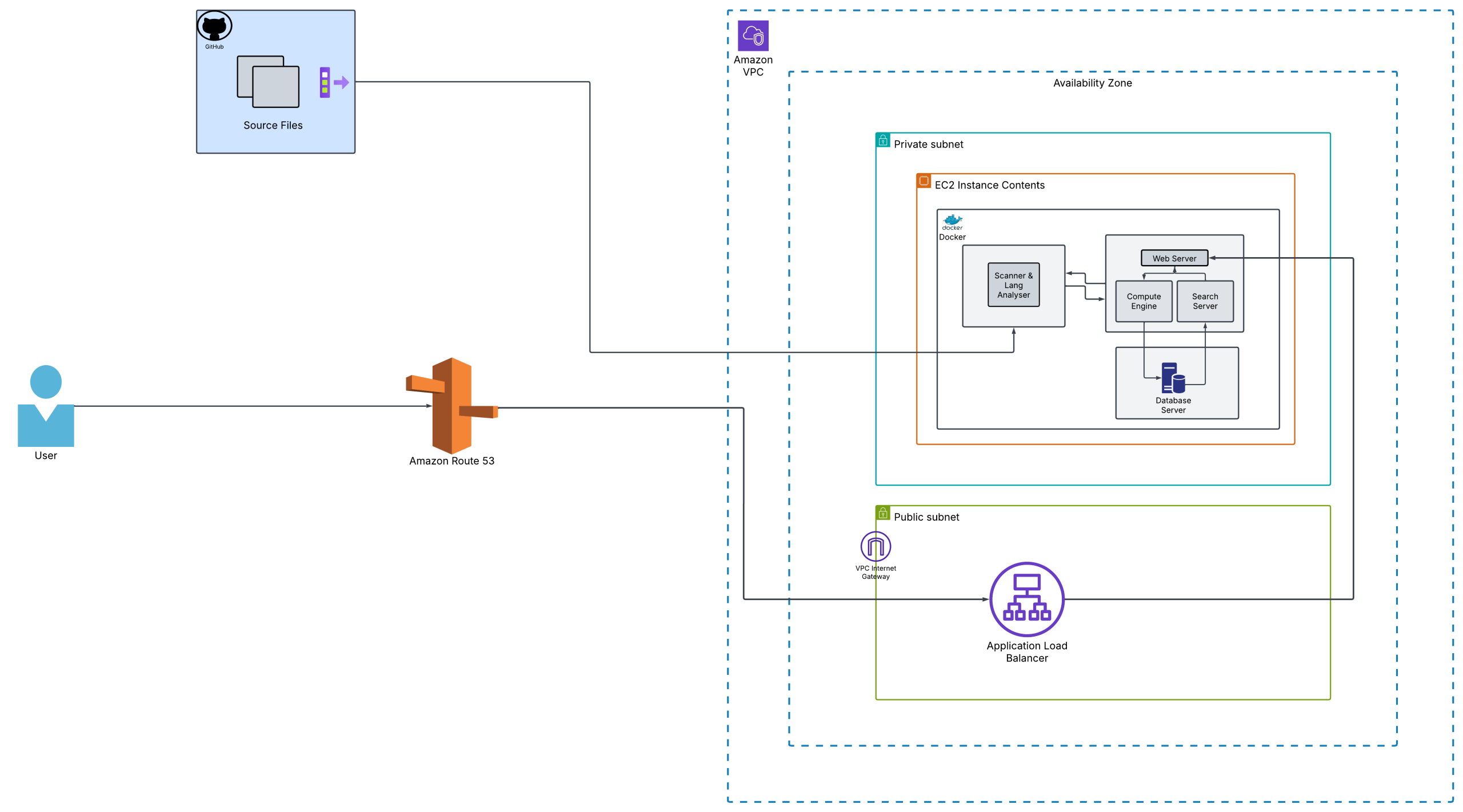
Infrastructure Overview:
The setup involved:
- Ubuntu EC2 Instance – Running Dockerized SonarQube
- Docker & Docker Compose—to manage SonarQube and its dependencies
- AWS Application Load Balancer (ALB)—Handling HTTPS traffic and SSL termination
Deployment Process—Step by Step
Setting Up the Infrastructure
The first step was to provision an Ubuntu EC2 instance with sufficient resources to run SonarQube efficiently. Given that SonarQube requires considerable memory and CPU, we chose an Amazon EC2 t3.medium instance, ensuring adequate performance.
We configured the instance with a security group that allowed only necessary traffic, specifically enabling:
- SSH access for remote management.
- SonarQube’s default port (9000) to allow internal application traffic.
- HTTP and HTTPS traffic for external access via the ALB.
Installing and Running SonarQube in Docker.
To avoid the complexity of manual installations, we used Docker to run SonarQube. This allowed us to spin up the application quickly and ensured that we could easily manage updates and configurations.
A key component of this setup was integrating PostgreSQL as the database backend. Instead of using SonarQube’s built-in database (which is not recommended for production), we configured it with an external database, ensuring data persistence and reliability.
Once SonarQube was running, we accessed the web interface using the instance’s public IP on port 9000 to verify that the application was operational.
Configuring AWS Application Load Balancer for HTTPS
Instead of manually setting up Nginx’s reverse proxy, we leveraged the AWS Application Load Balancer (ALB) for SSL termination and load balancing.
Steps Taken to Set Up ALB
Creating the Load Balancer:
- We launched a new Application Load Balancer via the AWS Management Console.
- We configured it as internet-facing, ensuring public access.
Adding a Secure HTTPS Listener:
- We added a listener for port 443 (HTTPS).
- Instead of managing SSL certificates manually, we used AWS Certificate Manager (ACM) to provision and attach an SSL certificate.
Configuring the Target Group:
- We created a target group that included our SonarQube EC2 instance.
- We mapped the target group to port 9000, as SonarQube runs on that port.
Updating Security Groups:
- We ensured the ALB’s security group allowed HTTPS (443) inbound traffic.
- We restricted direct access to the EC2 instance, and allowed access only through the ALB.
Once the ALB setup was completed, we tested access to SonarQube via the custom domain linked to the ALB. We ensured that HTTPS termination was working correctly.
Key Challenges and Resolution Strategies
1. SonarQube Performance Issues
- Problem: Running SonarQube on a lower-tier EC2 instance led to frequent crashes due to memory constraints.
- Solution: Upgrading to t3.medium resolved performance issues by providing adequate RAM and CPU resources.
2. Redirecting HTTP to HTTPS
- Problem: The application failed to automatically redirect users accessing the service via HTTP (port 80) to HTTPS.
- Solution: AWS ALB does not provide automatic redirects, so we enforced HTTPS at the application level and via ALB listener rules.
3. Persistent Data Storage
- Problem: Data lost during container restarts.
- Solution: We configured Docker volumes for data persistence, ensuring reports and configurations remained intact.
Architecture Diagram:
 Benefits of This Approach:
Benefits of This Approach:
By the end of the POC, we had a fully operational and secure SonarQube setup with the following benefits:
- Automated Code Quality Checks: We analyze every code change to prevent bugs and vulnerabilities from reaching production.
- Secure HTTPS Access: AWS ALB ensures encrypted traffic without requiring manual SSL configurations on the instance.
- Scalability and High Availability: ALB allows us to add more SonarQube instances if needed.
- Simplified Maintenance: With Docker and AWS-managed services, maintenance overhead is reduced significantly.
- Seamless CI/CD Integration: Developers get real-time code analysis feedback, improving overall software quality.
Insights and Action Plan:
This Proof of Concept (POC) successfully demonstrated the feasibility and effectiveness of deploying SonarQube with Docker on AWS, leveraging Application Load Balancer (ALB) for secure HTTPS access. By containerizing SonarQube and utilizing AWS infrastructure, we achieved a scalable, secure, and maintainable solution for continuous code quality monitoring.
The results of this POC reaffirmed that automated static code analysis can significantly improve code reliability, security, and compliance within a DevOps-driven development lifecycle. The combination of SonarQube, Docker, and AWS ALB provided us with a flexible and efficient approach to integrate code quality checks seamlessly into our existing workflow.
Action Plan
To maximize the benefits of this implementation, we plan to:
- Deploy this setup in a production environment with Auto Scaling and High Availability measures to support enterprise-grade workloads.
- Integrate SonarQube with our CI/CD pipelines (Jenkins, GitHub Actions, GitLab CI/CD, etc.) to enforce automated code quality checks at every stage of the development lifecycle.
- Enable advanced security plugins for deeper vulnerability detection and compliance tracking, ensuring adherence to industry best practices like OWASP Top 10 and SANS Top 25.
- Automate SSL certificate renewal using AWS Certificate Manager (ACM) to ensure uninterrupted secure access to SonarQube.
- Enhance monitoring and logging by integrating SonarQube with AWS CloudWatch and centralized log management systems for better observability and troubleshooting.
Conclusion:
In an era where code quality directly impacts user experience and business continuity, implementing automated and scalable solutions for static code analysis is no longer optional—it is essential. This blog outlined a streamlined approach for deploying SonarQube Community Edition using Docker on an Ubuntu EC2 instance, fronted by AWS Application Load Balancer (ALB) for secure HTTPS access.
As we move forward with production deployments, CI/CD integration, and enhanced monitoring, this foundation positions us to maintain high standards of code quality, security, and compliance, essential pillars of sustainable software delivery.

