Meet Vikki Ellison

Presidio has a variety of IT solutions and vendors. I never get bored working with only one technology/vendor. This opportunity allows me to continue to learn and obtain new certifications.
Meet Vikki Ellison
Tell us about the road that led you to Presidio.
I was on the customer side of Presidio for about 15 years, and during that time I was introduced to the Presidio Contact Center team. During my time working with that team, I was amazed at how professional and easy to work with they were. When I finished up my customer side contract role, I decided to interview with the Presidio team I had been working with, and I have been here for the past 7 years.
What attracted you to Presidio?
What attracted me to Presidio was the family atmosphere that Presidio embodies. On both my team and in the greater company, the culture is all about people helping people. You can always reach out to anyone in the company and know that they have got your back
What is a tech trend that you are excited about?
Right now, I am excited about AI. Both from what we are doing on my team and for personal use. There is so much potential for what AI can do. On my team, we are just at the very beginning of utilizing Google’s AI to improve analytics, and it’s really exciting to kick off.
What is your hobby and how does it apply to the work you do at Presidio?
I consider myself a teacher, I have always loved teaching. I was a preschool teacher, and I think that set me up for success at Presidio. I think if I can teach preschoolers, I can handle anything! I also was a lecturer at the University of Denver, and I taught project management as well as soft skills. It was always great to see people grasp those concepts.
One thing that I carry on in my role at Presidio from being a teacher is staying updated with the trends so I can be as much of an expert as possible in training my team. I find that I learn a lot from my team too, that’s what teaching is all about.

Our team slogan is “do something great every day”. That is what I have felt since the day I joined.
Ramakrishnan H
What led you to Presidio?
Presidio hosted a local hackathon. They gave us a set of problems for us to solve and a time limit to see how many problems we could crack. The prize was an interview with the company. This challenge was a breakthrough, and many people like me were able to gain a foot in the door and provide meaningful contributions and skills. I was working for another company and knew, by participating in the hackathon, that I wanted to join Presidio.
What is it like working at Presidio?
I’m always challenged and I’m always on the lookout to learn new skills and find new things that I can do better. We are constantly receiving new opportunities to explore and there are endless opportunities. Our team slogan is “do something great every day”. That is what I have felt since the day I joined.
What is your superpower/unique talent?
I know the right questions to ask and every meeting I am in. This helps me immensely on finding the exact requirements for any given project. If it is for a customer working through pain points or a general call before I wrap up every meeting making sure I have asked the right questions. I have created a knack for asking the right questions over the journey of 7-plus years of experience. This helps me do my job much more efficiently.

Traveling gives us a chance to interact with different people. When you interact with different people and cultures, you pick up on the energy and learn new things.
Meet Renukha L
How do you view Presidio culture?
Presidio treats its employees like family. They help us with our careers goal as well as our personal goals. If I have any issues, I can openly speak with my manager. There is also a great sense of work/life balance.
What is it like working at Presidio?
Here at Presidio, I can learn across different practices and upskill my knowledge. I can continuously learn and am encouraged to take on new challenges to enhance my skills daily.
What’s inspires you and your work right now?
Traveling gives us a chance to interact with different people. When you interact with different people and cultures, you pick up on the energy and learn new things. These are life lessons no one can teach us. I visited a globally renowned theme park on a recent vacation to France. I was inspired and energized by the beauty of the park. When developing applications, I always ensure they are fully functional and, above all, visually appealing.

I‘m a hobby farmer…It’s like working in technology; it’s always changing. Every season there’s a new challenge or something new to forecast for.
Amanda B
What is your superpower? How does this superpower align with your work here at Presidio?
I’m a hobby farmer. Farming is an adventure where you can have a lot of success and a lot of failures. The failures can either cost your family food or time, or money. I grow between 30 to 40 different crops on a very small scale, but managing all those different ecosystems is very challenging. Every year comes with failures. I’ve had to learn over the seasons what works best.
It’s like working in technology; it’s always changing. Every season there’s a new challenge or something new to forecast for. Is it going to be a wet or sunny year? Did we have a wet or dry spring? All these different factors come into it, and you must adapt.
Do you have a special talent?
I am a Smart Hula-Hooper. My hula hoop is an internet of things (IoT) LED hula hoop that creates light images while you’re using it. I use code to make the light modes and the remote control to change the settings. The hoop also gets software updates from the manufacturer when plugged into a PC.
What is the best career advice you have ever been given?
I had a sales coach who told me that I had the gift of gab and that I shouldn’t be afraid of it but rather that I should find power in it and use it to my benefit. Before in my life, I always feared speaking up, especially as a young woman working in tech. This advice helped me find my own and it helped me come into myself as a person and recognize that my opinions matter and what I say has value.
How do you view Presidio culture?
Presidio is probably my favorite company I’ve ever worked for. I think the reason for that is working at Presidio is kind of like watching words get written on a page while reading them out loud at the same time. So, you have input and output in the very same moment and that just creates this electricity and this vibe of everybody humming and buzzing.



Presidio has given me a long-term career and prospects for continued growth. Presidio provided, and continues to provide, me with the room to grow (personally and professionally) and develop through experience, education, and coaching.
Meet Maria C
What attracted you to Presidio? And what keeps you here?
Presidio has given me a long-term career and prospects for continued growth. Presidio provides me with the room to grow (personally and professionally) and develop through experience, education, and coaching. The management teams I have worked with take a genuine interest in your life, your experience with your colleagues and customers, and your career progression.
What is it like working at Presidio?
No day is ever the same – the technologies, customers, and teams involved in projects I manage are constantly changing. It can be hectic at times, however, there is always a supportive environment, to discuss challenges and celebrate the wins, with peers or management.
What is your superpower/special talent? How does superpower align to your work here at Presidio?
Organization – I can organize any room or occasion.
I can think logically and quickly about how a schedule or plan should look, what information is needed, and how it should be stored so everyone who needs it has the access. Lists are my best friend.

Presidio is a place where people are super energetic. It keeps you on your toes, and it’s super exciting to be among the team. There are always opportunities to grow and explore.
Meet Vimal P
What attracted you to Presidio? And what keeps you here?
I was really looking for a new kind of challenge and for a company where I could show my impact. I came from a larger organization and couldn’t see how I impacted the company and what we did.
What is your superpower/special talent? How does it align with your work here at Presidio?
I love watching documentaries, following geopolitics, reading about diverse topics ranging from history to psychology and, most importantly, spending time with my family & children.
Being aware of the person on the other side of the conversation makes me think, feel and help them by whatever means I can. This has helped me build relationships with clients and the Presidio family. Reading on diverse topics has also enabled me to see things from different perspectives, look for opportunities and think long-term.
How do you view the Presidio culture?
Presidio is a place where people are super energetic. It keeps you on your toes, and it’s super exciting to be among the team. There are always opportunities to grow and explore. Another important point is the leadership is accessible and there to give feedback and help you continue to evolve.

The people are very important here – our people drive our business.
Rob P
What is a lesson that you’ve learned over the past few years?
The biggest lesson I’ve learned in the last two years is to take a step back sometimes and just reflect on what’s going on, what the situation is, and then the people and everybody involved in that situation or the business in general. It is important for me to take a step back and just reflect internally, how am I doing? Is there something I could be doing better? How can I help out my team better? How can I help out my business better?
What is Presidio’s culture like?
The people are very important here – our people drive our business. We work with a variety of people overcoming difficult problems and complex situations. Working through these challenges, you bond and become more of a family with everyone instead of just coworkers.
What’s energizing you in your work right now?
The people driving our success, and of course my own team, they’re amazing. I’m proud of things I’ve accomplished here, but I’m more proud of the things that they’ve accomplished here. I love seeing them grow. I love seeing them meet their career goals and I love seeing them be successful. With some of the great feedback I get from our customers, it makes me makes me feel like a proud father.
What is your superpower and how does it align to your work here at Presidio?
I’d have to say empathy. That’s empathy with our customers and understanding what they’re going through to help us drive them to their successful outcomes. It is important to have empathy and understanding of what they’re trying to go through so that we can help them.

Whether it’s a dusty old pair of cross-country skis or a state-of-the-art data center running mission-critical apps, there is always something new to learn and optimize.
Meet Bill O
What attracted you to Presidio? And what keeps you here?
Presidio acquired the successful local VAR I was working for and welcomed me into the Presidio family with open arms. This move provided me with countless opportunities to learn new skills, meet new thought leaders, and expand my reach to new customers around the country. Best of all, Presidio is one of the few “engineering first” IT solutions providers in the marketplace today, which is one of the things I love about working at Presidio.
What is energizing you and your work right now?
The biggest mystery for most of our customers is how to intelligently migrate their workloads to the various public cloud providers. Considering there are now 7 “R”s to cloud migration, I don’t blame them! My biggest focus right now is learning how to help customers migrate as cost-effectively as possible to the public cloud where it makes sense and modernize their on-premises infrastructure for everything else.
What’s energizing you in your work right now?
The people driving our success, and of course my own team, they’re amazing. I’m proud of things I’ve accomplished here, but I’m more proud of the things that they’ve accomplished here. I love seeing them grow. I love seeing them meet their career goals and I love seeing them be successful. With some of the great feedback I get from our customers, it makes me makes me feel like a proud father.
What is your superpower/special talent?
I am a hard-core cross-country skier. I recently became a PSIA-certified cross-country ski instructor at the Loppet Foundation, one of our local nonprofit outdoor adventure centers. I teach private and group lessons to new and developing skiers from December through March while competing at a half dozen Midwest Nordic ski races.
How does superpower align with your work here at Presidio?
My passion is to positively impact people in learning new skills, refining their existing skills, and getting the most out of the equipment they have today. Whether it’s a dusty old pair of cross-country skis or a state-of-the-art data center running mission-critical apps, there is always something new to learn and optimize.
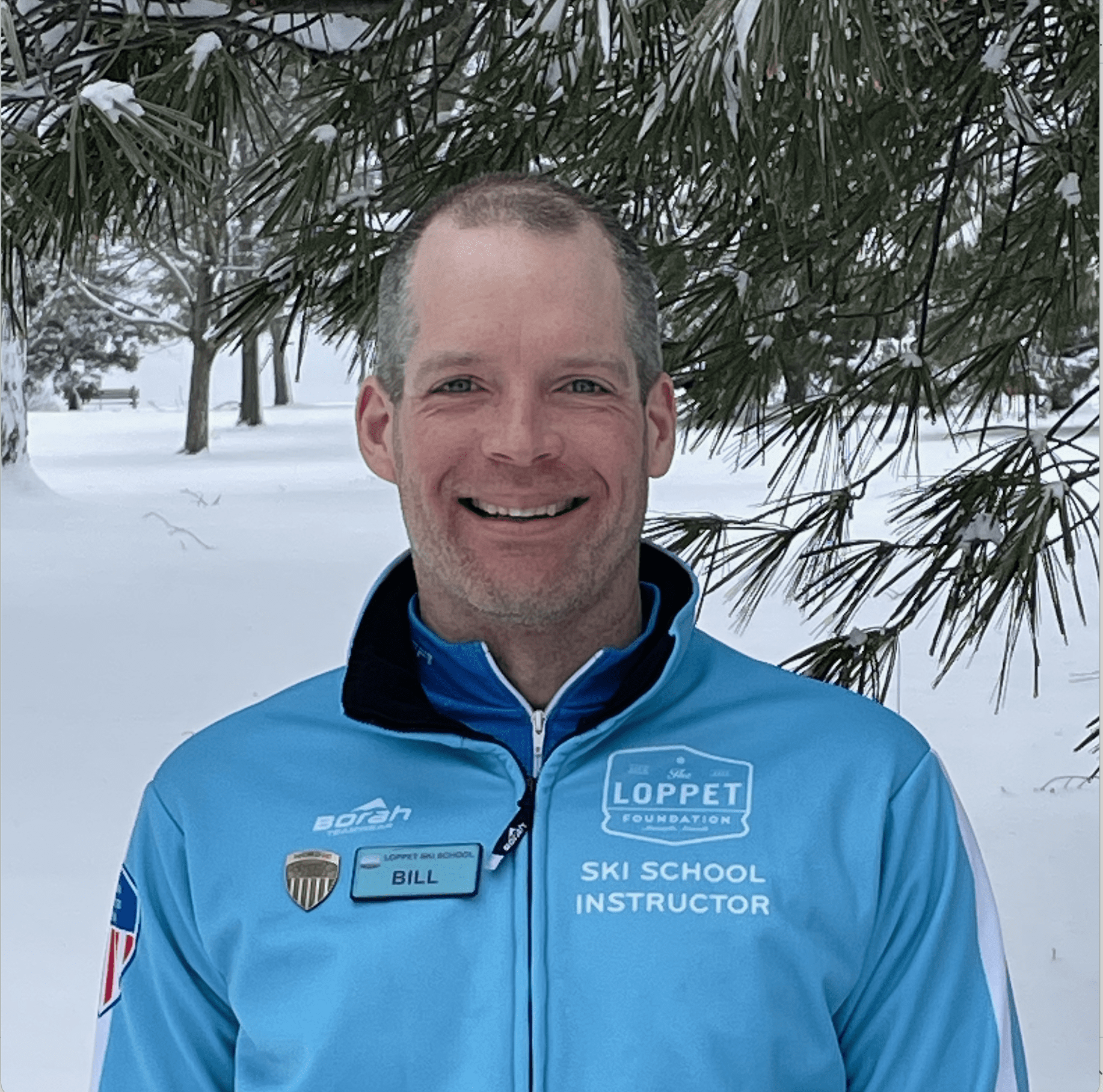

When there’s an emergency, I typically will jump in. This really ties into being there for our customers when the worst happens.
Meet Dave T
What do you do at Presidio?
I get to meet with our clients to talk to them about cybersecurity, where they are today and where they need to be.
What drives you personally?
I was in the Marines for a long time, so I have always had a responsibility to act. When there’s an emergency, I typically will jump in. This really ties into being there for our customers when the worst happens. They must feel that comfort knowing they have somebody who does this for a living, they have somebody right here that knows exactly what is going to happen for the next six weeks while we handle this situation.
Our video crew caught up with Dave at our Global Exchange event to find out what he likes best about Presidio culture and the superpower he brings to Presidio.

Being in a project management organization is a perfect fit for someone who loves to plan and pay close attention to detail. I love working with people and understanding the full scope of a project down to the smallest details.
Meet Nikki B
What attracted you to Presidio? And what keeps you here?
I enjoy the people I work with and learning all about the different applications and processes behind the scenes for Presidio. I appreciate the opportunity to create and improve internal IT processes for my team and help drive change within our organization.
What is it like working at Presidio?
“If you learn something new every day, you can teach something new every day.” – Martha Stewart I am lucky to learn new things daily here, which makes my job so exciting. I share that knowledge with my team, and we work together to update and improve our processes.
What is energizing your work right now?
There are so many new initiatives that the different teams want to do to improve their processes to serve our customers better, and this requires help from the IT team.
What is your superpower?
I am an over-the-top party planner. I love creating decorations and all the little touches myself. I own way more décor than I would like to admit. Pick a theme; I probably have a bin dedicated to it.
How does your superpower align with your work here at Presidio?
Being in a project management organization is a perfect fit for someone who loves to plan and pay close attention to detail. I love working with people and understanding the full scope of a project down to the smallest details.


Playing drums is a lot like working through projects, in that, you must have coordination between your own tasks as well as play in concert with your team/band. Only then will you be able to make great music or get seamless failover for your application workloads across DCs.
Meet Steve D
What attracted you to Presidio? And what keeps you here?
I was drawn to Presidio for its vast exposure to top engineering talent as well as a wide variety of new technology solutions. These same things keep me engaged along with the satisfaction of being able to truly help our clients.
What is energizing you and your work right now? What drives you?
The love of learning how things work. This is especially true with new technologies that I can lab up and experiment with to see how they can be used to solve a business challenge.
What is your superpower/special talent?
Music! I am a drummer and come from a very musical and artistic family. I have been on tour across the U.S. and Canada playing in previous bands and was even out on a month and a half long tour.
How does superpower align with your work here at Presidio?
Playing drums is a lot like working through projects, in that, you must have coordination between your own tasks as well as play in concert with your team/band. Only then will you be able to make great music or get seamless failover for your application workloads across DCs.

Life at Presidio is fast-paced, interesting, and full of great challenges. There is room to learn and grow, to really hone my skills on large project delivery.
Meet Nate G
What is life like at Presidio?
Life at Presidio is fast-paced, interesting, and full of great challenges. There is room to learn and grow, to really hone my skills on large project delivery.
What’s energizing you and your work right now? What drives you?
The opportunity to work on new technologies and working with customers to move to modern architectures. I love looking at the big picture and finding ways to optimize and modernize customer’s infrastructures.
What is your superpower/special talent?
Whenever I am not working, I enjoy being active and outdoors. I am a qualified rock climbing instructor and run a National Climbing competition. I also mountain bike, snowboard, ski and surf if the weather if good enough.
How does superpower align to your work here at Presidio?
I feel that the common thread between these activities is developing a skill through hard work, persistence and patience. These sports have also taught me how to assess risks and how to approach a difficult situation with a clear head and focus.

I am energized to bring new solutions and see growth in cloud delivery, which is the trajectory we want to be on for our customers.
Meet Doug G
What path led you to Presidio?
I was part of an acquisition, so my journey here was a little different. Presidio was one of our key partners, so it was a natural fit for us. My old company was all about the cloud, but now we can bring In a complete suite of services and capabilities for our clients.
What’s energizing you these days?
I am energized to bring new solutions and see growth in cloud delivery, which is the trajectory we want to be on for our customers. We get to see so much more of Presidio now after the acquisition. We get to provide greater value to our customers and engage more with all of our teams.
What is your superpower?
My superpowers have evolved over the years. Right now, I am focusing on being a manager and listening to the people reporting to me, my peers, and our customers and sellers. Focusing on management and collaboration are my superpowers right now.

Never has technology been so closely integrated – from carrier to cloud services, to app developers, to infrastructure service owners. The silos of the past are collapsing and just like the succession of life in nature, new growth is all around us.
Meet Paul G
What is energizing you and your work right now? What drives you?
I am energized by the generational shift we are currently undergoing. Never has technology been so closely integrated – from carrier to cloud services, to app developers, to infrastructure service owners. The silos of the past are collapsing and just like the succession of life in nature, new growth is all around us as the decentralized nature of work and personal life creates new technology paradigms.
Tell us about a tech trend you are excited about.
I am currently very excited about human-machine interfaces. AR and VR are starting to mainstream, and I think we will see direct brain interfaces commercialized in the next two decades. I am equally excited about the expansion of freedom throughout the world with technologies such as block chain absorbing political power that used to be held by nation states.
What is your superpower/special talent?
My superpower is the ability to dream big and manifest that dream into a practical reality. I brainstorm in VR, model in CAD, test my ideas with AR, and work with both new and classic tool sets to pull things from the virtual world into the real.
How does superpower align with your work here at Presidio?
I use this superpower for woodworking at home, but the same type of ability is fundamental to providing value for my customers. Instead of envisioning a piece of furniture trapped in wood, I can see a future for their businesses where technology alleviates the pain and pressure that comes from operating the technologies that drive their businesses.
See Paul G’s superpower at work below.

Here, everybody is looking for the best possible solution for the customer and making it as innovative and scalable as possible so the solution can be leveraged for years to come.
Meet David H
How is life at Presidio?
The culture here is as different as day and night from all the other previous roles I’ve ever had. Our culture at Presidio is about work-life balance.
What’s energizing you and your work right now? What drives you?
Everybody’s passion at work is really what energizes me. Everybody is looking for the best possible solution for the customer and making it as innovative and scalable as possible so the solution can be leveraged for years to come.
What is your superpower/special talent?
I did a small stint as an amateur MMA fighter. That experience alone, just being in a ring fighting, takes confidence. It gives you the boost in life to break through barriers you think you have.
Tell us about a tech trend you’re following.
The tech trend I’m really into right now is automation, especially when it comes to like cloud technologies. Being able to take the mundane things that engineers are used to doing day by day and being able to deliver that faster, more efficiently is exciting.

Photo: Dave H. back in his MMA fighting days.

Presidio has a variety of IT solutions and vendors. I never get bored working with only one technology/vendor. This opportunity allows me to continue to learn and obtain new certifications.
Meet Andrzej Z
Tell us about the road that led you to Presidio.
I arrived in Ireland in 2007 and worked as a chef for six years. I moved, completed IT courses, took an IT internship in the financial sector, and obtained a junior sysadmin role in the same company where I interned. Three years after, I joined Presidio.
What attracted you to Presidio? And what keeps you here?
Presidio has a variety of IT solutions and vendors. I always enjoy working with more than one technology/vendor. This opportunity allows me to continue to learn and obtain new certifications.
What is life like at Presidio?
Fun and rewarding!
What is your superpower/special talent?
Apart from doing IT after work, I play guitar and I’m a qualified pastry chef.
How does superpower align with your work here at Presidio?
My superpower gives me confidence in my abilities! Presidio also hosts bake-off charity events couple times a year where I participate.

Working on a car’s restoration – it is all about paying attention to detail, learning new skills, and not being afraid to take something apart so that you can put it back together better than it was. Those are all skills you must have to be successful in IT.
Meet Tom L
What do you do at Presidio?
I work with an exciting group focused on bringing new, diverse people into our world of IT and engineering while helping to increase the efficiency of our Presales organization. In addition, I serve as the Chairperson of the Presidio Distinguished Professionals (PDP) Program.
What attracted you to Presidio? And what keeps you here?
Everyone likes being part of a growing company and being able to do that with people you like to work with is what keeps me here. Many of the people that I work with have become friends outside of work. I’ve been given great opportunities here, and I always felt this company rewards positive, creative, and motivated people.
What is energizing you and your work right now? What drives you?
We are building a team of “early career” Presales Engineers who will become that next generation of senior superstars. We are recruiting talent based on attitude and aptitude and training them to help build their skills in all the aspects of technology that Presidio sells.
What is your superpower/special talent?
Outside of work, I am very active in the collector car world. I buy, sell, and restore cars – mostly pre-1972 cars, and most are pre-WW2. My oldest car is a 1912 Auburn, and I am currently restoring a 1959 Gemini Formula Jr race car.
How does superpower align with your work here at Presidio?
Working on a car’s restoration – it is all about paying attention to detail, learning new skills, and not being afraid to take something apart so that you can put it back together better than it was. Those are all skills you must have to be successful in IT.


At Presidio, we are storytelling and building a narrative. We are focused on helping customers achieve business outcomes.
Meet Jake F
What attracted you to Presidio?
My dad was previously a delivery engineer for Presidio and is now on the Inside Presales team. He told me, “Jake, this is a company where you can make your career, a company that is going to enable you,” and that’s how I got started here.
What’s energizing you and your work right now? What drives you?
Freedom. Right now, it is the freedom to explore innovative technology trends. I feel like a pioneer sometimes on the new frontier.
Our video crew caught up with Jake F. at our global Exchange event to find out what Jake likes best about Presidio and his superpower.
How does your superpower align to your work at Presidio
At Presidio, we talk to a customer, and at the end of the day, we are storytelling and building a narrative. We are focused on helping customers achieve business outcomes. My superpower is talking to customers and getting feedback to drive that narrative forward.
Tell us about the mental health matters Employee Resource Group.
I co-lead the Mental Health Matters ERG (Employee Resource Group). Mental health awareness is a topic that people want to talk to about, but it can be challenging to discuss. We all have a desire to talk about it (mental health). That’s why we have created this ERG – to serve as a common place where our employees could start the conversation, promote employee mental health and provide resources to aid in positive change.

Being up to speed with technology is a destination – my job is to help figure out the directions.
Meet Leanna A
What attracted you to Presidio? And what keeps you here?
I want to be able to support the local government, and I love being an IT Solutions provider. I was also inspired to join because my first and second levels of leadership were women, and my 3rd level was a person of color. I need to be able to see myself in a company.
What’s energizing you and your work right now?
My customers. I love knowing that I’m making a real difference in how we support my fellow Washingtonians. We can support them and make positive, REAL change.
What is your superpower/special talent?
Research! I call it “social media mining.” I’ve learned to research people/things/places ahead of time and learn SO MUCH. It’s really fun.
How does superpower align with your work here at Presidio?
I use this to understand my clients’ needs and who they are. It is important to know what drives your clients so you can be flexible to meet their needs where they are instead of pushing them to be where they SHOULD be. Being up to speed on technology is a destination – my job is to help figure out the directions.

Here’s Leanna showing off another superpower, being an aerialist.
Think, work and achieve. Whatever I want to achieve, I start by just thinking about it, and then I start working towards it and that will help me to achieve it.
Meet Manish S
What is your fondest memory you have at Presidio?
We had this one event called ‘Presidio One’. I met many of my brilliant colleagues there, it was an event filled with both technical and fun events. At the end, we had a ton of great new ideas and had become closer as a team and as a Presidio culture.
In your personal life, what is/are your hobbies and why are you passionate about them?
I love reading books and writing poems and articles. I have published my collection of poems in book form. Apart from this, I also love to share my knowledge with tech communities, and create YouTube videos and blogs to spread tech knowledge.
How do your personal hobbies translate to the work you do at Presidio?
My hobbies really help me get involved in the many initiatives at the Presidio. I love to write and have written several technical blogs for Presidio’s website, and I am currently volunteering for an India side blogging initiative. I love to accept challenges, which helps me in my project work. I love to take opportunities and work through them.
What is a quote that you live by?
“Think, work and achieve”, I live my life with this quote in mind. Whatever I want to achieve, I start by just thinking about it, and then I start working towards it and that will help me to achieve it.
Gratitude is the gateway to joy. I want my team to know I appreciate their contributions to our success.
Meet Monica B
What do you enjoy most about working for Presidio?
Hands down – the people! Presidio has some of the best people in this industry within our organization. I have had the fortune of making incredible connections at Presidio and working on remarkable teams.
How do you view Presidio culture?
Presidio has a great culture, and we are working to make it even better (together)! One thing I love about Presidio is that Presidio cares about the people that work here. We have a culture of people here who not only care but want Presidio to be the best and continuously make improvements to achieve that.
What’s a rule(s) that you live by?
There would be two. The first would be “Gratitude is the gateway to joy,” and the second is, “You miss 100% of the opportunities you don’t take.”
The gratitude quote – It is easy to get wrapped up in everything around you when there is always so much going on. I want my team to know I appreciate their contributions to our success as a business. I must also remind myself how grateful I am for everything I have around me.
The second rule is one that I am consistently adapting and learning to be braver and take my mom’s old advice….”The worst they can tell you is no…and if you are asking, you only have to gain and not lose.”
What inspires and drives you?
Making an impact. I want to make a difference. This is most likely because I was raised by a teacher. It’s hard for me to sit and do nothing. I want my kids to be proud of what I do (even when they don’t understand it). I love being a part of something bigger than myself and making contributions to help influence positive change for the future.

Life is all clouds. When a cloud comes in, good or bad, sit through it because it will change.
Meet Angela L
Why did you choose to work at Presidio?
Of all the places I interviewed, I know this might sound cliché… Presidio seemed like the happiest, most positive place. I got the impression the company is very team-oriented, and there are a ton of opportunities to grow personally and with the team.
In your personal life, what is/are your hobbies and why are you passionate about them?
I write young adult fantasy novels. As a parent, I often read the same stories my kids do! Reading was an activity that my son and I really enjoyed. There was one story I started telling him when he was very young, and one night I got to thinking, “What happened to the mother in the story?” So, I started writing it down. I shared it with my son, and he was so excited about it. Since then, the stories have continued, and now I have published five novels.
How do your personal hobbies translate to the work you do at Presidio?
I love creating stories that energize people and make them feel good. For my job at Presidio, when I can create something for someone on my team and it makes them smile, that makes me feel good.
What is a quote that you live by?
My husband and I attend silent retreats focusing on living in the now. Our teacher once said something that stuck with me. He said, “Life is all clouds.” When a cloud comes in, good or bad, sit through it because it will change. You can’t control a cloud up in the sky. You can’t grab onto it, change it, or force it into something it’s not. Mindfulness is letting go of the things you cannot control. Just like good and bad experiences in life, each moment is temporary. Live it, and let it pass.

Presidio has a variety of IT solutions and vendors. I never get bored working with only one technology/vendor. This opportunity allows me to continue to learn and obtain new certifications.
Meet Alan H
Why did I choose to work at Presidio?
I chose to work at Presidio because of their commitment to innovation and technology solutions. While my background lies in film, I completed my Masters in screenwriting in 2018, having worked in retail management throughout my Student life. Presidio’s emphasis on leveraging technology to drive business success resonated with me, as I saw an opportunity to apply my creative skills in a unique and meaningful way within the IT industry.
My hobbies and passion:
In my personal life, I am deeply passionate about filmmaking. I spend most waking moments outside of my day job working on my filmmaking, be it writing new scripts, chasing funding for the next project or indeed project managing the post production life of films already completed. I am passionate about telling stories about social injustice, with narratives that try to encapsulate the experiences of those living on the fringes of our society.
How my hobbies translate to my work at Presidio:
My passion for filmmaking translates well into my work at Presidio. Through my creative background, I bring a unique perspective to the team, enabling me to approach projects with a creative mindset. Whether it’s developing engaging team narratives or designing visually appealing presentations, my expertise in storytelling and visual communication allows me to add value to the projects I work on. The Boxing keeps me healthy and fit to tackle the everyday challenges we all face in the workplace.
Quote I live by:
“Never be the one to tell yourself no, let someone else do that”

We have a chance to really change the world. Everywhere I turn, I’m working with different SLED teams and there is a lot of energy, opportunity, and passion to provide solutions that impact our world. That excites me a lot.
Meet Dan L
What attracted you to Presidio?
I had heard quite a bit about Presidio. A well-renowned expert in the field talked to me about the unique things Presidio is doing, and the difference Presidio is making. As I researched it further, I was impressed with the level of talent, expertise, scope, involvement, and deep relationships that Presidio had with several state and local governments and the private sector.
What motivates you?
We have a chance to really change the world. Everywhere I turn, I’m working with different SLED teams and there is a lot of energy, opportunity, and passion to provide solutions that impact our world. That excites me a lot.
What is your superpower/special talent?
I love writing. I’ve been blogging in the industry for more than 15 years and write for Government Technology magazine. I write for CISO magazine. I’ve written three books. I just coauthored a book that was a bestseller on Amazon for six weeks.
How does superpower align with your work here at Presidio?
I’m passionate about writing and I really enjoy public speaking. So, being able to speak all over the world in front of different audiences to offer cybersecurity answers and solutions that really can help our clients aligns well with my superpower.
In addition to his work at Presidio, Dan is an accomplished writer. Read his recent blogs on GovTech.com.

Throughout my career I have worked on being passionate because people still buy from people.
Meet Dave A
What’s energizing you at work right now?
What is energizing me right now is having our team move away from sort of the traditional discussions and having more conversations around cloud, application development, and data.
Tell us about a tech trend you’re excited about.
Across the board, it’s the move to cloud. I’m excited for our team to be able to help customers innovate in the cloud. That’s the kind of cool trend I’m seeing out there. That’s our fun right now.
Our video crew recently caught up with Dave A. at our Global Exchange Sales event. We asked Dave what life is like at Presidio and the superpower he brings to Presidio.

It’s a community of individuals bringing their own talent trying to improve the business. We come together and are better together.
Meet Camen M
What attracted you to Presidio?
I wanted to see what it was like to be on the diversity side of tech companies. I’ve grown up knowing Presidio. My mom has worked at Presidio for 18 years, and all the individuals she’s working with have known me since high school. To see all of her co-workers still striving in this environment attracted me because I knew there was an opportunity for me to grow and come in to put my twist on what I would like to see in the diversity equity inclusion department.
How would you describe Presidio culture?
It is a welcoming culture. It’s a community of individuals bringing their own talent trying to improve the business. We come together and are better together. It is also an evolving culture as we go into bringing new people on and expanding internationally as well. We’re doing great things. We’re striving to make sure that our people are seen, heard, and valued.
What would you say is energizing you? What you’re in your role right now.
There’s so much negativity going on in this world. It’s important that I can come to work and try to create a positive atmosphere for individuals that may not have that environment anywhere else. I want to get to the space where we’re here at Presidio, and we’re able to realize that it takes one another to get results. What energizes me is getting up every day, knowing I have the autonomy to create new ideas, initiatives, and activities and partner with great people who can make these things come true.
What is your superpower or special talent that you bring to Presidio?
My special talent is interpersonal relationships. It goes back to me being an educator; it also goes back to growing up in a family of servant leaders. I also coach football. I’m here to serve. Being able to connect with different people from different backgrounds and come up with the same results is my superpower.

How we’re influencing people’s lives or clients’ lives is something that gets us jazzed up!
Meet Rob K
What is a lesson you have learned over the past few years?
I have learned that sometimes you must be forced into change. And the fact is, now, with all this acceleration of technology adoption, we’re in a state of perpetual change. You must be flexible.
What are some trends you are excited about?
Obviously, I have a ton of tech trends I am excited about! I am excited about sustainability and Diversity & Inclusion initiatives, specifically how we are making investments internally as an organization.
Our video crew recently caught up with Rob K. at our Global Exchange Sales event. We asked Rob what is energizing him at work right now and his superpower.

My work at Presidio benefits greatly from my positive energy and I believe it inspires others to be the best version of themselves!
Meet Gloria D
What attracted you to Presidio? And what keeps you here?
I’ve been at Presidio for four years and having previously worked at various Cisco partners, I can confidently say Presidio is the best of the best. Presidio has a backing large enough to assist the most prestigious clients across many industries and is still agile enough to successfully drive internal change and serve our clients’ ever-changing needs.
What is it like working at Presidio?
Life at Presidio provides me with daily challenges, flexibility, and creativity.
What’s energizing you at work?
I get energized helping to create and lead programs that employees benefit from both personally and professionally. Seeing the value delivered through our training and enablement programs, firsthand, is rewarding and inspires me to continue growing!
What is your superpower/special talent?
My superpower is my infectious positive energy. I am extremely passionate, motivated, and enthusiastic with a love for life. My work at Presidio benefits greatly from my positive energy and I believe it inspires others to be the best version of themselves!

I have unlimited enthusiasm for just about everything. I love when a customer brings us a big problem. It is great to come in with fresh eyes to help solve that problem together.
Meet Nate L
What attracted you to Presidio? And what keeps you here?
We are in the business of solving problems for customers, so the work is always interesting and stimulating. The people I work with are incredible – everyone is so smart and talented, but at the same time, so friendly and enjoyable.
How is life at Presidio?
We employ some of the best engineering minds in the marketplace, so there is always demand for more work. With new products coming to market frequently, vendors routinely bring us their latest technology to pilot it in our labs. At the same time, there’s a strong sense of family here – our executives stress the importance of good work-life balance. It is a great work-hard / play-hard culture and a lot of fun.
What is energizing you and your work right now? What drives you?
The rate of change in new technology. You are always learning something new, so the job is never the same each day.
Tell us about a tech trend you are watching.
Medical researchers upload staggering amounts of complex data to the cloud and then run different analyses against it. I’ve helped a few Biotech companies with their cloud strategy and security, seeing how they’re using it to cure Alzheimer’s or fight cancer. It’s humbling when you realize you helped them to make an impact.
What is your super power? How does superpower align with your work here at Presidio?
I get really excited to learn new things, and I tend to pick up a lot of new hobbies. One is cooking – I can cook better than most grandmothers (sorry, Mimi). During the pandemic, I was cooking like we were at a restaurant 4 or 5 nights a week which was a lot of fun. I have unlimited enthusiasm for just about everything. I love when a customer brings us a big problem. It is great to come in with fresh eyes to help solve that problem together.


I feel very valued here, and it is great to see the hard work noticed by management, who are always offering praise.
Meet Gary M
What attracted you to Presidio? What keeps you here?
All the people inside the business are friendly and welcoming. Presidio is also one of the top global digital solutions and services providers, so I knew it would be a fantastic opportunity to expand my skills and knowledge and to learn from some of the best. All the management and colleagues are extremely helpful, and understanding, and I feel privileged to work here.
What is it like working at Presidio?
Life is great here at Presidio. We have a great work/life balance. The management team is excellent and very accommodating. I am happy to be part of the Presidio team.
What is one thing that makes you proud to work here at Presidio?
The overall culture of the company. From my very first day, everyone was accommodating and approachable. It feels like one big family. I feel very valued here, and it is great to see the hard work noticed by management, who are always offering praise.
What is your superpower/unique talent?
My superpower/unique talent is kickboxing. I have been training in Kickboxing for the last 15 years. I am currently part of the Irish National Kickboxing Team. I am ranked number 2 in the world in the WAKO world rankings. Along with one of my teammates, we became the first two Senior Males in Irish Ring Sport history to win the Wako European Championships for Ireland. I aim to continue competing over the next few years and retire as an Irish Olympian.

What I do outside of Presidio, smashing through that concrete, having the right balance of technique and power and speed is what I bring to Presidio!
Meet Julie R
What do you do at Presidio?
I manage a whole bunch of awesome people that deliver great services to our customers. In addition to that, I run the team that configures and stages projects that ship from a centralized facility, so our engineers don’t have to be onsite.
What have you learned at Presidio?
I have learned to be resilient and to make sure that we adapt. You never know what kind of circumstances we are going to encounter. Our customers have changed a lot, so our engineering lives have changed a lot. We need to know If we’ve made a different choice or a decision that we need a change, that we can easily change it and start a different path.
What do you enjoy most about working at Presidio?
I love the people of Presidio. I believe in our mission and our core competencies. I see Presidio as an extended family.
Our video crew caught up with Julie at our global Exchange event to ask what life is like at Presidio and the superpower she brings to Presidio. Find out her answers by watching the video below!

Joining an Employee Resource Group really opens your community up and you start to see, I’m not the only one – I’m also everywhere in the company.
Meet Melissa D
What is your perspective on life at Presidio?
Regardless of whether you’re at the corporate, regional or working remote, you still get that very comfortable environment where everyone knows everyone’s name and if they don’t, they learn it. There is always a very welcoming environment. There is always an effort to create that connectivity between the teams. Just because we are in different places doesn’t mean we disconnect.
What is your superpower?
My superpower and probably my biggest motivator is just being a single mom so that the hat that comes with juggling your professional career, your personal life being a parent, and creating a solid foundation. I think that’s probably my superpower. But I also do have learning disabilities I’ve had to really cope with in my professional career. I look at those more as more of an advantage, though. It gives me the opportunity to see things from a different perspective and to effectively do my work probably differently than a lot of other people.
How does your superpower align to your work at Presidio?
That advantage allows me to step back and calculate things to make sense to me. I know naturally, if you ask me now to pull the data, it’ll take me a while to process. So I create platforms from scratch. I spend a lot of time at the forefront, creating a system that will help pull critical information as quickly as my colleagues need me to. It’s just it’s how I need to work, and it helps me do my job better. If I can do my job better, you get better results from me, and we all end up benefiting from that.
What has your experience been participating in our Employee Resource Groups?
As a person of color, as a woman in technology, it was very important for me to see other people who can identify similarly. Sometimes feels like you’re not as visible. Joining an ERG really opens your community up and you start to see, I’m not the only one – I’m also everywhere in the company. These resource groups are really giving a whole to a lot of different people that sometimes may not feel like they have a home.We want to continue along this path to give everyone a home that they can identify with.

“Do Something Great. Everyday!” This has been my mantra.
Meet Arvind M
What is life like at Presidio?
Work and fun are inextricable at Presidio. The culture encourages people to engage in fun events while ensuring client deliverables are on track. We celebrate festivals by wearing traditional dress or having a potluck lunch as well.
What’s energizing you and your work right now? What drives you?
“Do Something Great. Everyday!” From the day I joined till now, this has been my mantra. I enjoy managing complex projects, architecting elegant solutions for customer problems, and raising the bar constantly with my team.
Tell us about a tech trend you’re watching.
AI/ML is picking up speed. One of my experiences has been automating golf scoring to replace a manual effort of a person. The solution used an intelligent system with cameras to process feeds and take appropriate actions. Businesses have started exploring what Machine Learning could solve.
What is your superpower/special talent? How does it align with your work here at Presidio?
My superpower is being resilient to challenges and having strong, persuasive skills to lead people. Being resilient helps me navigate and scale myself quickly, be it technical or managerial challenges. Along with my persuasive abilities, it has helped me mentor next-generation leaders within Presidio.

Sometimes it seems as if there are more solutions than problems. On closer scrutiny, it turns out that many of today’s problems are a result of yesterday’s solutions.
— Thomas Sowell
Meet Syd S
In your personal life, what is/are your hobbies and why are you passionate about them?
I am an avid cyclist. I have been riding since my college days. I ride rode, mountain, and most recently – gravel biking. I have ridden in the deserts of Botswana, hills of Bosnia-Herzegovina, isles of Greece, shores of Europe and now seek out the trails of the United States.
How do your personal hobbies translate to the work you do at Presidio?
Like cycling, there are times where you are alone and times when with a group. So, you must either grind yourself up a hill or down a long, winding road on your own, or there are times when you have assistance from the group, who encourage you and can even “pull” you by riding in front and providing a wind break.
Do you have any goals you are working towards this year? Either personal or in your job?
I have reach one already. After 30+ years serving our great nation, the United States, in a military capacity, I, Colonel Shinn, retired in June 2023. My next goal is to be there and give away my daughters on their wedding days; so far, one down and one more to go. I figured the weddings would be enough for this year.
What is a quote that you live by?
I have a few and drove my Soldiers and family crazy with my colloquial sayings. But I suspect I really have two I live by.
Be Bold, Be Brief, Be Gone: which translates, be confident in what you are saying and know the facts to stand by them; speak succinctly but specifically when presenting your topic; and do not seek accolades of your accomplished speech on your topic but move on as any compliments or questions will follow.
Sometimes it seems as if there are more solutions than problems. On closer scrutiny, it turns out that many of today’s problems are a result of yesterday’s solutions. –Thomas Sowell
Make sure to understand the long-term ramifications of the choices and decisions one makes today. We humans, most of the time, want to solve the problem immediately, but the immediate may be the detriment of the distant. As a PM, I always need to understand how the potential decisions I make affect the future efforts to reach the goal.

Syd Posing with his wife

It’s a community of individuals bringing their own talent trying to improve the business. We come together and are better together.
Meet Cyndi B
Why did you join Presidio?
Presidio has an appetite for growth, and this stood out to me during the interview process. I love that the Presidio continued to focus on that through the pandemic. It is what sets us apart from our competition, and makes us stand out to our clients.
What keeps you here at Presidio?
The people keep me at Presidio. I don’t think of working at Presidio as a job, I think of it as it’s a career choice that I made. And I love it here. My long term plan is to remain here.
The team I work with closely really is a tight knit group, from the leadership team down to the individual market teams, whether as in California and the Pacific Northwest or Texas or the Midwest, everybody’s just really built really solid relationships. We make sure that one another achieve our goals, both personally and professionally.
What’s your special talent or hobby?
I have an award winning salsa! I competed in a contest about five years ago with a local radio station, and lo and behold, I was the sole winner for Southern California!
However, where I get passion from is my two grandkids. I am so happy to be a younger grandparent who has the energy and the ability to spend time with my grandkids and and appreciate them in their childhood in a different way than I appreciated spending time with my own children. I love being able to take a step back and enjoy my time with them and prioritize my time with them. It is what drives me every day.
How do your passions align with Presidio?
Prioritization. It is important to prioritize family time and the work I do here at Presidio. If I am with the kids, I prioritize that time. And then when it’s Presidio time, I prioritize that time. At the end of the day it is rewarding to see my team reach their goals, just like it is rewarding to laugh and play with my grandkids. It is important to have a healthy mix of work and life.

UJIMA is the BIPOC network serving Presidio employees of color. We create a safe space for employees of color to share their voice and experiences and engage in peer mentorship.

VETs provides career growth, networking, and resource to Presidio employees who identify as veterans or supporters of veterans. We are particularly focused on supporting veterans who are transitioning from the service to corporate life.

WONDER is a supportive community for women of diverse backgrounds to advance their skills and grow their leadership potential. We seek to foster an environment that promotes innovation, safety, trust, and acceptance.

Pride is a community where LGBTQ employees and allies can come together to create community, promote awareness, and celebrate diversity.

Mental Health Matters is focused on promoting employee mental health by raising awareness, reducing stigma, and sharing resources and guidance amongst peers.

I‘m a hobby farmer…It’s like working in technology; it’s always changing. Every season there’s a new challenge or something new to forecast for.
Meet Amanda B
What is your superpower? How does this superpower align with your work here at Presidio?
I’m a hobby farmer. Farming is an adventure where you can have a lot of success and a lot of failures. The failures can either cost your family food or time, or money. I grow between 30 to 40 different crops on a very small scale, but managing all those different ecosystems is very challenging. Every year comes with failures. I’ve had to learn over the seasons what works best.
It’s like working in technology; it’s always changing. Every season there’s a new challenge or something new to forecast for. Is it going to be a wet or sunny year? Did we have a wet or dry spring? All these different factors come into it, and you must adapt.
Do you have a special talent?
I am a Smart Hula-Hooper. My hula hoop is an internet of things (IoT) LED hula hoop that creates light images while you’re using it. I use code to make the light modes and the remote control to change the settings. The hoop also gets software updates from the manufacturer when plugged into a PC.
What is the best career advice you have ever been given?
I had a sales coach who told me that I had the gift of gab and that I shouldn’t be afraid of it but rather that I should find power in it and use it to my benefit. Before in my life, I always feared speaking up, especially as a young woman working in tech. This advice helped me find my own and it helped me come into myself as a person and recognize that my opinions matter and what I say has value.
How do you view Presidio culture?
Presidio is probably my favorite company I’ve ever worked for. I think the reason for that is working at Presidio is kind of like watching words get written on a page while reading them out loud at the same time. So, you have input and output in the very same moment and that just creates this electricity and this vibe of everybody humming and buzzing.



What I do outside of Presidio, smashing through that concrete, having the right balance of technique and power and speed is what I bring to Presidio!
Meet Julie R
What do you do at Presidio?
I manage a whole bunch of awesome people that deliver great services to our customers. In addition to that, I run the team that configures and stages projects that ship from a centralized facility, so our engineers don’t have to be onsite.
What have you learned at Presidio?
I have learned to be resilient and to make sure that we adapt. You never know what kind of circumstances we are going to encounter. Our customers have changed a lot, so our engineering lives have changed a lot. We need to know If we’ve made a different choice or a decision that we need a change, that we can easily change it and start a different path.
What do you enjoy most about working at Presidio?
I love the people of Presidio. I believe in our mission and our core competencies. I see Presidio as an extended family.
Our video crew caught up with Julie at our global Exchange event to ask what life is like at Presidio and the superpower she brings to Presidio. Find out her answers by watching the video below!

Director, Strategy and Innovation at Presidio
Phil Filippelli, Director, Strategy and Innovation, leads Presidio’s Innovation Practice helping clients such as the NHL achieve their digital transformation goals. He has more than three decades of experience successfully delivering desired business outcomes through technology. Phil is a developer at heart and has led teams across a variety of industries in creating and implementing innovative and leading-edge solutions. Prior to joining Presidio, he was Vice President of Innovation at EHE Health, and held technology leadership roles at CVS Health and TD Synnex. He holds a Bachelor of Science from Central Connecticut State University and lives in Tampa, FL.

Client VP at Presidio
George Santa, Client VP at Presidio, is focused on helping clients align their business with the right technology to drive meaningful outcomes. He partners closely with customers such as the NHL to drive digital transformation and help them meet their goals. George joined Presidio in 2007 as a Senior Account Manager. He earned a Bachelors of Arts from Tufts University and lives with him family in New York.

NHL Executive Vice President, Business Development & Innovation
David Lehanski is the Executive Vice President of Business Development & Innovation for the National Hockey League, responsible for leading the League’s technology and innovation initiatives through the establishment of corporate partnerships, state-of-the-art technology solutions and new revenue.
Lehanski joined the NHL in 2005 and has been instrumental in building the most advanced technology solutions in sports. He has been a key driver in establishing the League’s world class technology infrastructure through creating partnerships with tech giants Apple, Amazon Web Services (AWS), SAP, Sportradar, Rogers and Verizon. These partnerships and tremendous advancements in technology and innovation have not only well positioned the NHL to expand and advance both the game and the fan experience, but they have also helped to fuel the League’s remarkable business growth and record revenues.
Lehanski has been at the forefront of the development and implementation of the NHL’s innovative EDGE (Puck and Player Tracking) technology, which received a prestigious Alpha Award for Best Sports Innovation at the 2022 MIT Sloan Sports Analytics Conference. Under Lehanski’s leadership, the League and NHL EDGE made history alongside ESPN and the Disney Channel with the NHL Big City Greens Classic, the first-ever live, animated NHL game telecast, featuring the Washington Capitals vs. New York Rangers. The hugely popular NHL Big City Greens Classic demonstrated how data from NHL EDGE can create entirely new fan experiences for a younger audience in collaboration with best-in-class partners.
Over the past several seasons, Lehanski has been focused on developing new solutions with industry-leading technology providers including Apple, AWS, SAP, Sportradar, Rogers and Verizon to improve and enhance the game for players, coaches and officials, as well as for fans and for the League’s broadcast and corporate partners. This has included the debut of AWS’s Shot and Save analytics and Face-Off Probability and leveraging Verizon’s cutting-edge 5G technology in-arena.
Lehanski was instrumental in the creation and implementation of the NHL’s groundbreaking in-arena coaching system introduced in 2017 – in collaboration with Apple – delivering real-time video highlights to coaches on the benches of every NHL arena. He also helped to develop the next phase of the NHL’s in-arena coaching system with the launch of the SAP-NHL Coaching Insights App for iPad, providing access to real-time, customized data and player statistics during the game on home and away benches in all 32 arenas.
Inside the NHL, Lehanski leads the NHL’s internal Innovation Team. Made up of internal experts from business development, strategy and information technology, the Innovation Team helps to advance the game of hockey by developing and implementing technology-driven solutions focused on the business and the game. Under Lehanski’s leadership, the Innovation Team has hosted three Technology Showcases – one during CES in Las Vegas in 2019 at T-Mobile Arena showcasing Puck and Player Technology, the second in 2022 at Prudential Center in New Jersey, demonstrating how the League can leverage 5G technology, and the most recent in March 2023 at Climate Pledge Arena in Seattle, exploring new experiences leveraging cloud technology. Each showcase was a pilot of futuristic technology solutions being developed by the NHL in collaboration with several leading technology providers to enhance the in-arena and at-home viewing experience.
Since joining the League in 2005, Lehanski has played an important role in the League’s path to close to $6 billion in annual revenues, establishing landmark partnerships for the NHL with some of the biggest global brands including AWS, Verizon, Apple, SAP, Dunkin, Honda, PepsiCo, Geico, Discover, Enterprise, Cisco, and MillerCoors, among many others. Lehanski was also one of the drivers in the League’s progressive approach to sports betting, helping to secure strategic partnerships with sportsbooks including MGM Resorts International, FanDuel and Caesars.
Before joining the NHL, Lehanski served as Vice President of Marketing Solutions at Clear Channel Advantage where he worked with Fortune 500 advertisers/marketers to develop, sell, and activate fully integrated media/marketing solutions that leveraged all of Clear Channel’s assets. Previously, Lehanski was the co-founder and Vice President of HallOfSports.com, an online company focused on the distribution of sports memorabilia and collectibles with a long-term goal of consolidating the industry. He also spent several years as a consultant on the agency side at SFX Sports and Clarion Sports & Entertainment.
Lehanski was named to SportsBusiness Journal’s Forty Under 40 Class of 2012, recognizing executives for excellence and innovation in their industry before the age of 40. He earned a B.A. with a major in economics from Bowdoin College and currently resides in Ridgewood, NJ with his wife Alison and two sons, Eddie and Leo.

Our team slogan is “do something great every day”. That is what I have felt since the day I joined.
Ramakrishnan H
What led you to Presidio?
Presidio hosted a local hackathon. They gave us a set of problems for us to solve and a time limit to see how many problems we could crack. The prize was an interview with the company. This challenge was a breakthrough, and many people like me were able to gain a foot in the door and provide meaningful contributions and skills. I was working for another company and knew, by participating in the hackathon, that I wanted to join Presidio.
What is it like working at Presidio?
I’m always challenged and I’m always on the lookout to learn new skills and find new things that I can do better. We are constantly receiving new opportunities to explore and there are endless opportunities. Our team slogan is “do something great every day”. That is what I have felt since the day I joined.
What is your superpower/unique talent?
I know the right questions to ask and every meeting I am in. This helps me immensely on finding the exact requirements for any given project. If it is for a customer working through pain points or a general call before I wrap up every meeting making sure I have asked the right questions. I have created a knack for asking the right questions over the journey of 7-plus years of experience. This helps me do my job much more efficiently.

Traveling gives us a chance to interact with different people. When you interact with different people and cultures, you pick up on the energy and learn new things.
Renukha L
How do you view Presidio culture?
Presidio treats its employees like family. They help us with our careers goal as well as our personal goals. If I have any issues, I can openly speak with my manager. There is also a great sense of work/life balance.
What is it like working at Presidio?
Here at Presidio, I can learn across different practices and upskill my knowledge. I can continuously learn and am encouraged to take on new challenges to enhance my skills daily.
What’s inspires you and your work right now?
Traveling gives us a chance to interact with different people. When you interact with different people and cultures, you pick up on the energy and learn new things. These are life lessons no one can teach us. I visited a globally renowned theme park on a recent vacation to France. I was inspired and energized by the beauty of the park. When developing applications, I always ensure they are fully functional and, above all, visually appealing.
Presidio has a variety of IT solutions and vendors. I never get bored working with only one technology/vendor. This opportunity allows me to continue to learn and obtain new certifications.
Meet Alan H
Why did I choose to work at Presidio?
I chose to work at Presidio because of their commitment to innovation and technology solutions. While my background lies in film, I completed my Masters in screenwriting in 2018, having worked in retail management throughout my Student life. Presidio’s emphasis on leveraging technology to drive business success resonated with me, as I saw an opportunity to apply my creative skills in a unique and meaningful way within the IT industry.
My hobbies and passion:
In my personal life, I am deeply passionate about filmmaking. I spend most waking moments outside of my day job working on my filmmaking, be it writing new scripts, chasing funding for the next project or indeed project managing the post production life of films already completed. I am passionate about telling stories about social injustice, with narratives that try to encapsulate the experiences of those living on the fringes of our society.
How my hobbies translate to my work at Presidio:
My passion for filmmaking translates well into my work at Presidio. Through my creative background, I bring a unique perspective to the team, enabling me to approach projects with a creative mindset. Whether it’s developing engaging team narratives or designing visually appealing presentations, my expertise in storytelling and visual communication allows me to add value to the projects I work on. The Boxing keeps me healthy and fit to tackle the everyday challenges we all face in the workplace.
Quote I live by:
“Never be the one to tell yourself no, let someone else do that”

VP, IT Infrastructure & Support Services Delaware North
An Emmy Award-winning IT executive with an expansive background across sports broadcast media, sports venues, and hospitality sectors, currently leading the charge in Infrastructure and Services at Delaware North, a global hospitality powerhouse. This seasoned professional combines a rich history of technological innovation and strategic leadership to enhance operational efficiencies, guest experiences, and service delivery. With a keen eye for cutting-edge solutions and a commitment to excellence, they play a pivotal role in maintaining Delaware North’s reputation as a leader in the hospitality industry, ensuring the seamless integration of technology and services across its diverse portfolio.

Vice President, North America Storage Platforms and Solutions Sales Dell Technologies
Ken Dougherty is Vice President, North America Sales, Storage, Platforms and Solutions for Dell Technologies. Ken brings 20-plus years of experience leading sales at storage and enterprise software companies, Ken excels at building high performance sales teams and driving significant revenue growth. Prior to joining Dell EMC, Ken served as Vice President of North America Sales at Kaminario leading direct and indirect sales. Prior to Kaminario, Ken led the HP Big Data sales organization for the Eastern U.S. and Canadian markets where his team delivered double digit growth and consistently overachieved sales goals throughout his six-year tenure.
In 2011, while at HP, he was recognized as Global Sales Leader of the Year. Ken also led the Eastern and Canadian Region at Compellent, establishing new markets and delivering triple digit revenue growth. Ken began his sales career and spent 10 years at Storage Tek in various sales and sales management positions. Ken and his wife, Kendra, live in Hopkinton with their four children: Tyler, Chase, Brooke and Mary-Kate.

Vice President of Solutions Architecture Presidio
Ron Kenney, Vice President of Solutions Architecture, is responsible for the Presales Engineering organization in the North. As a Presidio Distinguished Engineer, Ron is a thought leader contributing to the development of transformational, next-generation solutions for Presidio’s clients across the organization. Ron has held multiple engineering and leadership positions since joining Presidio in 2008 including Network and Security Architect, Solutions Architect, Principal Consultant and Engineering Delivery VP.

VP, Security Sales Cisco
Vice President, Americas Security Sales Cisco As VP of Americas Security Sales, Scott is responsible for leading growth in the United States, Canada, and Latin America go-to-market, strategy, and execution across the security portfolio. His team’s focus is to help customers reduce their risk profile and drive top customer and partner business outcomes with a security platform approach. Before joining Cisco, Scott held sales and leadership positions for 20+ years at Imperva, Forcepoint, Palo Alto Networks, most recently serving as VP of Americas Sales at Deep Instinct.
Prior to that, he spent nine years at Palo Alto Networks in several sales leadership positions, including overseeing sales execution and operations as VP in the Global Account organization. Scott is a graduate of Drexel University and currently resides in sunny Delray Beach, Florida. Scott and his wife, Alice, met in college and are very proud parents of Abby and CJ, students at Texas Christian University.

CISO and Head of Infrastructure - Abrams Capital Management, LLC
Frank LoBello is a seasoned technologist with over twenty years of experience. He currently holds the role of CISO and Head of Infrastructure for Abrams Capital Management where he oversees all of the underlying technology and cybersecurity initiatives. He has been with Abrams since 2009 and has lead the firm through many major projects including multiple datacenter moves, SASE implementation, and cloud migrations. Whenever he can escape his busy schedule, Frank can be found on the golf course, bike trail, or local car show. He is also an avid gamer and enjoys many modern and classic titles.

VP of Cybersecurity and IT - Evolv Technology
Peter Vittands is seasoned cybersecurity and IT leader with 25+ years experience leading security to enable business success and currently operates as the VP of Cybersecurity and IT at Evolv Technology.
Evolv’s mission is to make the world a safer place for people to gather. Evolv is privileged to help their customers mitigate risk and keep the public safe using industry-leading AI-powered detection solutions.

AVP IT Infrastructure Operations - NETSCOUT Systems
Michael Kelly is a seasoned IT Professional with 30+ years of experience across a number of technology functions. He has spent the past 13 years managing a diverse set of IT Operations teams for NETSCOUT. Prior to joining NETSCOUT, Michael held a similar role for 12 years at EBSCO Publishing. I’m proud to say that my partnership with my friends at Presidio has been instrumental to my success.

Director - Cisco
Joe is an experienced sales professional with a passion for building strong, collaborative teams and driving results. He thrives in dynamic environments and has a proven track record of success in sales, particularly within the technology industry. Currently, Joe is a proud leader at Cisco Systems, a global leader in networking and communications technology.

SVP and Chief Information & Digital Officer - Hartford HealthCare
Joel L. Vengco is the Senior Vice President of ITS and Chief Information and Digital Officer (CIDO) at Hartford HealthCare (HHC) where he leads all technology operations and services, enterprise applications, and data and digital transformation initiatives across 8 hospitals, over 400 clinical sites, and 36K employees. Mr. Vengco has over 20+ years of informatics, technology, and healthcare innovation experience and is focused on harnessing the power of data and digital to transform care delivery to be more a personalized and orchestrated experience for patients.

SVP, General Counsel, Corporate Secretary & Acting CIO - Cerence
Jennifer is an executive leader for conversational AI for the automotive and greater mobility ecosystem with 25+ years of experience in the technology space. Leading and implementing iterative, transformative remapping of people, processes and technology to AI company’s top and evolving business needs, including systems, cybersecurity, cloud/tech infrastructure, procurement, project management and end-user support.

VP, Infrastructure & Cloud Services - FM Global
Brian Fortin serves as Vice President of the Infrastructure & Cloud Services division of FM Global’s Strategy & Business Enablement organization. Brian brings more than 30 years of experience in leading & transforming information technology environments and building long-term partnerships with business and technology stakeholders. In his current role, Brian is responsible for defining and developing enterprise-wide strategies to ensure the ongoing and future alignment of technology for modern cloud/DevSecOps, core infrastructure, cyber-security solutions, IT Service management and user-enabling technologies. In his free time Brian enjoys hiking, running, reading, travel and spending time with his three children.

Enterprise District Sales Manager - Dell Technologies
Tom is a passionate and accountable sales leader with a proven track record of partnering along side our customers to deliver successful outcomes. His current team is responsible for Dell Technologies’ Enterprise Preferred accounts in the Northeast. Tom and his wife, Meghan, currently reside in Boston. Outside of work, Tom’s hobbies include golf, sporting events, and family time in the Cape.

VP IT Infrastructure & Operations - DFW International Airport
Cornelius is an accomplished professional with extensive expertise in overseeing IT infrastructure and operations. Currently serving as the AVP of IT Infrastructure and Operations for DFW International Airport, Cornelius excels in telecommunications, system engineering, network management, and life safety systems. With a strong background in managing access control, CCTV systems, and public and private airport Wi-Fi, cellular, and radio networks, Cornelius is recognized for implementing robust IT solutions that ensure seamless operations and enhance security measures.

CTO - COCC
As Senior Vice President & Chief Technology Officer, Steve Reis plays a critical role in leading technology and infrastructure initiatives at COCC. Since joining COCC in 2008, Steve has held many different roles, starting as a Security DBA and leading to his current position, in which he is responsible for the COCC technology footprint and for ensuring infrastructure is ready for new client additions and new product offerings.
Steve has forecasted and strategically expanded COCC’s operations to ensure that COCC remains a top-tier technology organization. His technical ability coupled with his leadership and commitment to client service have made him an integral player at COCC. Steve has continually demonstrated that he can and will seek out the best technical solutions for COCC while keeping service levels top notch.

CIO - New England Biolabs
Lennox is a seasoned technology executive with 25+ years of consulting and corporate experience. He drives IT organizations to focus on value while delivering outstanding service to the company’s employees and customers. He has broad business acumen including in-depth expertise in operations, product management, supply chain, shared services and information technology. Within technology, Lennox has been responsible for all aspects of running a global IT organization, including application development, infrastructure operations, business intelligence, engineering support, and cyber-security.

Director, Cloud & Network Architecture - ElevateBio
Konstantine is the new Director of Cloud & Network Architecture at ElevateBio with nearly 20 years of experiences in networks and systems. His most recent position was with Center for Breakthrough Medicines where he was a Senior Solutions Architect. Prior to this Konstantine was the Critical Infra Lead at Takeda. Given the critical operational and information security aspect to this role, Konstantine will be reporting to Todd Hiser, Senior Director, IT Infrastructure and Operations, as part of leadership team, and dotted line reporting to Christian Hammer, Vice President, Head of Information Security IT.

SVP, Global IT Procurement & Contracts - IGT Global Solutions
Global SVP of IT Procurement, Communications, and Contract for office of the CIO. Responsible for CIO’s global budget across all technology.

Sales Director
Matt has worked in various sales positions over his 13+ years here at Presidio. The last 6 have been spent leading a team of 11 well tenured Account Managers as a Sales Director here in New England. Matt & his wife Julie currently reside in Portsmouth, NH. They are enjoying the empty nest lifestyle with their only daughter off at Bentley University in Waltham, MA.

Sales Director
Eric currently leads an experienced team of 7 sales professionals that align to our valued customers within Connecticut. Prior to joining Presidio in 2020, Eric spent nearly 10 years with Dell-EMC working with customers throughout New England. Eric earned a degree in Economics from Wheaton College and is a father to (3) daughters with his wife Laura.

Field CTO
Eric Vogelpohl brings 25 years of leadership and innovation in the IT sector, focusing on cloud services and advanced data analytics. His career spans significant roles, beginning with tours in enterprise IT at a major natural gas firm, where he honed his skills in the practical application of technology solutions to complex business challenges.
Eric served as the Managing Director of Tech and Strategy at a leading Seattle-based data and AI engineering firm for 6 years. In this role, he oversaw the adoption of cutting-edge data management and AI technologies and methodologies, demonstrating a keen ability to merge technical prowess with strategic vision.
Since early 2023, Eric has focused purely on both the underlying technologies and the practical business applications of Generative AI (GenAI).
Currently, as the Field Chief Technology Officer (CTO) at Presidio, Eric is dedicated to guiding Fortune 500 companies through the evolving landscape of Data and the use of GenAI. His role encompasses a blend of architectural expertise and strategic leadership, enabling him to effectively navigate and influence the future of technology in business.
Eric has an MBA from Oklahoma State University.

VP Director of Information Technology - GEI Consultants
Kevin has 20 years of Project Management and Business Consulting, Infrastructure management, administration and engineering. He’s worked in various industries including software development, healthcare, government, banking, insurance and AEC. Prior to GEI Kevin worked for companies including Liberty Mutual, TSA, Citizens Bank, Philips and more. Kevin has been with GEI going on 10 years.

Chief Architect - NETSCOUT Systems
Lewis Sharpe is the Chief Architect at NETSCOUT Systems, a leading provider of service assurance, security, and business analytics. He has been in the IT industry for over 20 years and has extensive experience in leading-edge technologies. His focus is on getting the most out of these technologies to drive business impact and help to develop innovative products.

PDM - AWS
Caitie is the lead Partner Development Manager for Presidio based out of Boston, MA, managing the relationship between AWS and Presidio. Prior to her almost 4 years at AWS, she spent time focusing on Strategic partner devlopment at Zerto and Navisite. Her Technology career began at EMC in the Channel. In her free time, you can find her coaching youth Basketball and Softball.

Senior Director - AWS
Bill Burns represents Amazon Web Services’ Worldwide Government, Education, and Healthcare Business. Bill is the Senior Manager for Higher Education and Healthcare accounts in Boston, leading a cross-functional team that consists of Account Managers, Consultants, Architects and Solutions Managers. Bill has spent the last 2 decades focused on helping Public Sector and Higher Education customers modernize, optimize and secure their enterprises.

Sales Director
George O’Connor currently manages a talented group of 9 sales professionals working with our valued customers in the New England region. George has been with Presidio for 5 years, prior he spent 10 years in Enterprise sales roles at both RSA Security & VMware (with a mobile app start up sprinkled in). George is a graduate of Bentley University & earned his MBA in ’09.& He’s a grateful married father of 3 with 2 boys at Villanova &a daughter in high school. In his spare time you can find him playing the drums or performing his side hustle as a janitorial services engineer for his wife’s Fitness Studio.

Head of Information Security & Technology - Alkermes
Ronan is a seasoned professional with over 25 years of expertise in Information Technology. As the current Head of Information Security and Technology at Alkermes, Ronan plays a pivotal role in safeguarding and advancing the technological infrastructure critical to the company’s operations. With a wealth of experience, Ronan has successfully navigated the evolving landscape of IT, implementing robust security measures and innovative technologies. Ronan is committed to ensuring the seamless integration of cutting-edge solutions in the pharma/biotech sector, contributing significantly to the intersection of technology and life sciences. A proven team leader and business partner with a track record of aligning Information Security, IT strategies and business needs in enterprise implementations, mergers, and acquisitions

Senior Vice President of Sales, Digital Business Solutions & Services
Kevin Fleurie is Senior Vice President of Sales, Digital Business Solutions & Services. He joined Presidio in 2009 as an account manager and has held leadership roles such as VP of Sales for the Public Sector and now heads up the Sales strategy for our cloud and digital go-to-market teams. Kevin holds a degree in business management from Colby Sawyer College.

Chief Solutions Officer
Dan O’Brien, Chief Solutions Officer, is responsible for Presidio’s comprehensive portfolio of technology capabilities including the development of offerings, strategic vendor alignment, presales and solutions architects as well as strategic acquisitions. Prior to joining Presidio in 2021, he was SVP of Global Commercial Presales at EMC where he started his career as a Hardware Engineer and rapidly progressed through their presales engineering organization holding various leadership and strategy roles. Dan holds a Bachelor’s degree in Electrical and Computer Engineering from Worcester Polytechnic Institute.

Senior Vice President of Sales, Northeast
Bryan Calder, Senior Vice President of Sales, Northeast is responsible for helping customers digitally transform and leading a regional team of outcome focused sales professionals. He joined Presidio in 2016 and has more than 20 years of experience in technology sales. Bryan graduated from Merrimack College and holds a bachelor’s degree in business management.
Chief Technology Officer
Robert Kim, Chief Technology Officer at Presidio advises clients on how to accelerate digital transformation and use technology to drive organizational outcomes. He evaluates IT trends and clients’ specific challenges with the goal of optimizing key business processes to improve end-user experiences, accelerate innovation and create market differentiation. Prior to joining Presidio in 2016, Rob held leadership positions at technology management and consulting firms, with roles in sales engineering, business development, operational excellence, and financial management. He graduated from Penn State with a Bachelor’s Science and earned his MBA at Drexel University.

Senior Director, Infrastructure - Vertex Pharmaceuticals
A passionate, self-motivated, Global IT professional, leading IT infrastructure and operations for international corporations through organizational growth and change. Specializes in the planning, design, and implementation of global technology solutions for corporations within the life sciences and consumer goods sectors. Strong understanding of infrastructure technologies and Manufacturing systems with a cloud-first mindset to help deliver on Operational Excellence and Service Level Management.
Experience building high-performance I&O organizations, through sourcing, retainment and external recruitment, while leading global alignment. Created scalable and secure infrastructure and services, leaning on automation and consolidation to optimize costs.

Director Network Services - Vertex Pharmaceuticals
A seasoned leader with 25+ years of experience managing and developing infrastructure teams across multiple industries. I’m currently working with Vertex Pharmaceuticals maturing the technologies that fuel our growth into new therapy areas including Type 1 Diabetes, Sickle Cell disease and pain management while support our Cystic Fibrosis patients.

Vice President & CISO - Security Mutual Life Insurance Company Of New York
Former USAF Veteran and current CISO for Security Mutual Life as of 2012, 23 years with Security Mutual Life. 30 years of IT experience. Christopher was born in Raised on the North Shore of Massachusetts and is a die hard Patriots, Sox, Bruins fan, despite living in Upstate NY for the past 25 years. Go Pats, Sox, Bruins

Chief Revenue Officer
Vincent Trama, Presidio’s Chief Revenue Officer leads a hands-on sales team dedicated to solving complex business challenges through digital solutions. He joined Presidio in 2012 and has held leadership roles driving a high performing team to generate new business and partner with customers to identify the best solutions for their evolving needs. Prior to joining Presidio, Vincent was Vice President of Sales at BlueWater Communication Group and Director of Northeast Sales at Visual Networks. Vincent holds a bachelors degree in Information Systems from Fordham University.

Senior Vice President of Sales, US SLED & West Named
Waheed Choudhry, Senior Vice President of Sales leads Presidio’s customer centric sales organization in serving U.S. State, Local and Education organizations (SLED) as well as the West Named Client Segment. Prior to joining Presidio in 2017, he served as President of the North America Organization at Dimension Data and served as President & COO of Nexus IS. Waheed holds a bachelors of science from California State University, Sacramento.
Vice President of Engineering
Sharan Gurunathan, Vice President of Engineering leads Presidio’s Global Delivery with a focus on cloud solutions and digital transformation through applications and data. This includes developing the company’s strategic global delivery roadmap and a key role as a sponsor of Generative AI and other Innovation initiatives, all focused on solving customer challenges and growing Presidio’s cloud practice. Sharan was a co-founder of Coda Global which Presidio acquired in 2020. He had held additional leadership roles such as the Country Manager in India for Avnet Services.

Avrio Consulting Group
Sridhar is a technical professional with diversified leadership experience in enterprise applications development and management, with over 25 years of experience in software development life-cycle for large multi-tier applications. He has deep expertise in directing and delivering large, complex, multi-year projects, with a matrix team of employees and consultants, driving efficiencies and processes in highly competitive markets. He leads various sized technology teams, including on and off-shore personnel. He is equally adept in performing at various levels of the ladder as needed – from solution architecture to c-level strategic thinking. Sridhar has been operating as the CIO of Matson Navigation Inc. for the past 2 years.

Avrio Consulting Group
As the CEO of Avrio Consulting Group, Rich helps clients drive digital transformation initiatives, data initiatives, organizational design and mergers & acquisitions. Current projects include leading the design and migration to a cloud-first modern data platform at a $5B company. Leading the integration of a newly acquired company at a midmarket direct-to-consumer clothing company. Recently completed a B2C replatforming initiative to modernize the customer experience. Also act as an advisor to the CEO and CIO on technology decisions at a mid-market company. Prior to starting Avrio Consulting Group, Rich was the CIO of Wheel Pros, focusing on digital transformation of a rapidly growing business. Rich successfully integrated six acquisitions that brought in $450 million in sales, while simultaneously replacing over 90% of legacy business systems, infrastructure, cyber security systems, and operational processes that enabled the business growth. Rich was a 2021 finalist for Denver CIO of the Year in the Enterprise category for the results achieved at Wheel Pros. Wheel Pros grew ~3x during his tenure. Previous to Wheel Pros, Rich has over 20 years of working across many disciplines in a Fortune 200 company, Bayer and Monsanto.

Head Of Product, AWS
Yaniv Ehrlich is the Head of Product for AWS Elastic Disaster Recovery and AWS Application Migration Service. Yaniv and his team are passionate about partnering closely with customers and partners to drive innovation and enable customers to move, improve and protect their data, applications, and systems. Yaniv has over 20 years of experience building and delivering technology solutions. Prior to joining AWS, he held various positions focused on business continuity, disaster recovery, and cloud migration.

Vice President Of Sales
Michael is the Vice President of Corporate Sales for The Central, West, and Latin American Sales Team at VMware. He is leading the transformation of the company under Broadcom, and wants to ensure that all of his customers consider VMware a Top 3 strategic partner.

Head of Partner Solutions Architecture, US and Canada
Divyesh Shah leads the Partner Solution Architects team focused on Consulting Partners for US at AWS. He and his team work with Partners to define Technology Strategy aligned with customer demands, Technology trends, and business goals. As a technology leader, Divyesh has successfully helped organizations drive business transformation by optimizing their business capabilities through adoption of technology for over 25 years across US, UK and APAC.

Lewis Brisbois Bisgaard And Smith
Tommy has grown to become a proven leader in information technology with over 15 years of experience in the legal vertical. He has helped Lewis Brisbois grow their technological core moving from a Novell network all the way to a Microsoft and cloud centric environment. Personally, Robert is married to his wife Ashley and has two daughters 6 and 2. He enjoys playing ice hockey and recently gotten in to projector mapping on his house.

AMN Healthcare
Todd Stott is a dynamic and driven global IT Executive with 35+ years of IT infrastructure engineering, enterprise architecture, and senior management experience. He is an effective team leader with a reputation for creating business cases and participating in activities to increase revenue and reduce IT expenses. Todd is a talented thought leader, knowledgeable in all industry best practices, and regularly interacting with C-suite to implement IT initiatives that drive key business objectives and help organizations grow. He is a results-oriented leader with excellent communication skills and a bias towards action. Todd is skilled in many areas including the following: Strategic Leadership | Cloud Enablement Azure – Google – AWS | Mergers & Acquisitions | Change Management | Business Process Improvement | Integrations | Vendor Relations Management | Cyber-Security | Risk-Compliance | Data Management | Data Center Operations | Stakeholder Relations

Laserfiche
Thomas Phelps IV is the CIO and SVP of Corporate Strategy for Laserfiche, the leading SaaS provider of intelligent content management and business process automation. As the CIO and SVP of Corporate Strategy, he has led strategic initiatives and technology innovation to transform the business, optimize costs, and enhance security and compliance. Under his leadership, Laserfiche was recognized as a visionary and leader by industry analysts, and was named a 2023 Gartner Peer Insights Customers’ Choice for Content Services Platforms. Previously, he was an Adjunct Professor at USC Marshall School of Business and the national entertainment and media champion for cybersecurity at PwC. Thomas is the Executive Chair of Innovate@UCLA. He is a Board Director on the audit and finance committees for Cal State University, Long Beach 49er Foundation. Thomas has co-authored/contributed to five books and been frequently quoted in the Wall Street Journal. He has also been cited in the Los Angeles Business Journal, Forbes, The Economist, The Enterprisers, CIO.com and Tech Target.

Sheppard Mullin
Robert has been at Sheppard Mullin for 37 years. He has served as a Managing Partner for the last 18 years and has Innovation/AI as part of my portfolio. Prior to becoming MP, Robert served as the Practice Group Leader for the Sheppard Mullin Litigation Group. Robert also has a background in class action defense of financial institutions. Robert attended UCLA and is married to his wife of 27 years (a USC alum) Together, they have 4 children aged 20-28. Robert’s Interests include: soccer (futbal), fly fishing and hiking.

DentalXChange
Navin Narayanan is the CTO of DentalXChange and has been with the company since the acquisition by EDI Health Group in 2004. Navin started his journey with DentalXChange as a Software engineer and has played a vital role in building almost every aspect of the DentalXChange platform. With the combined knowledge of dental, healthcare and technology he has led his team successfully and is always looking for new challenges. Navin has a Masters degree in Computer Science from the University of Southern California. He lives in Irvine, California with his family. When he is not working he likes riding his Triumph down the California coast or hiking with his wife and son.

Rain For Rent
Mike is the IT leader at Rain for Rent. He has spent more than thirty years working for and with equipment rental companies, twenty of which have been spent as a provider of Information Technology solutions to the equipment rental industry. Mike has sold, installed, and supported software systems internationally for more than one hundred rental companies. Rain for Rent is a provider of temporary liquid handling solutions including pumps, tanks, filtration, and spill containment. The company is known for its engineering expertise and its ability to provide effective solutions. Rain for Rent serves all 50 states, Canada, EU, and the UK more no less than 70 locations.

HealthEquity
Mervyn Lally is the senior vice president and chief information officer at Health Equity, an American financial technology and business services company. With over 20 years in the information technology field, he’s held previous positions at Experian, Land O’Lakes, and Ingersoll Rand. Lally has an associate degree in electronic engineering and a Bachelor of Science in Information Technology. Outside of tech, Lally enjoys golf, DIY projects, and spending time with his wife and three children.

Digicert
Chief Information Security Officer (CISO) Jeremy Rowley leads the company’s product development teams, driving innovation on the company’s certificate management platform as well as its delivery of leading solutions for protecting web servers, signing digital code and documents. Rowley also leads a team providing authentication, encryption and integrity solutions for the IoT, secure data exchange of medical records and other sensitive data, blockchain and post-quantum cryptography, among other emerging sectors. Rowley also represents DigiCert’s interests within various industry standards bodies and has authored several industry standards now in use. As part of DigiCert’s vision to lead its industry toward better and more trusted practices, Rowley actively participates in groups such as the CA/Browser Forum, IETF, Mozilla Forum, NIST and ICANN. Rowley was a key participant in drafting the CA/Browser Forum’s EV Guidelines, Baseline Requirements, and Network Security Guidelines, and he continues to draft new policies and guidelines today. Prior to joining DigiCert, Rowley worked as corporate counsel for another large Certificate Authority, helped build programs to achieve efficiencies within law firms, and served as a chief software architect for a global chemical software group. Rowley earned a JD from Brigham Young University as well as MS and BS of Science, Chemical Engineering at the same institution. Rowley is a member of the Utah Bar and currently serves as president of the Utah Bar Association’s Cyberlaw division.

Pima Community College
Jack has worked in the Information Technology space for more than 25 years, leading IT teams in both Private and Public sectors. He is currently the Chief Technology Officer for Pima Community College, providing leadership while overseeing IT Strategy for Security, Infrastructure and Enterprise systems. Jack retired from the US Army as a Chief Warrant Officer after 23 years on active duty in Tucson, Arizona where he now lives with his wife. Together they have 4 adult children that live in Phoenix and Tucson.

CHG Healthcare
Dean Lythgoe is a seasoned professional with expertise in cybersecurity, support services, infrastructure, and operations. Current role as Vice President of IT Services, Dean has played a pivotal role in steering the technological landscape for CHG Healthcare Services. Dean spent 25 years at Novell and has experience in both engineering and leadership capacities. Beyond the professional sphere, Dean is known for his passion for basketball. March Madness is a family tradition. In addition to being a spectator, Dean actively contributes to the basketball community as a high school basketball official.

CMC
Chris Bellew is the Sr. Director, IT Technologies, Engineering and Operations at CMC a global metals recycling, manufacturing, and fabricating enterprise. Prior to Commercial Metals he was the Director of IT Outsourcing at Blockbuster. Chris also worked for 7-Eleven in various Infrastructure management positions and business transformation project leadership. Chris is a member of the Board of Trustees for Dallas Academy a K-12 school that restores the promise of full academic enrichment for students with learning differences. In his free time Chris enjoys spending time with his wife and three children.

City Of Dallas
Dr. Brian Gardner is the Chief Technology & Information Security Officer for the City of Dallas. Dr. Brian joined the city in 2017 to develop IT Risk Management and Regulatory Compliance programs. Since taking on the role, he has implemented a risk-based framework for cybersecurity strategy to assess and mature the City’s security capabilities, assure regulatory compliance, and mitigate enterprise-wide technology and business risk. In addition, implementing the City’s first Cyber Fusion Center and Security Operation Center. Dr. Brian’s cybersecurity industry experience extends from global financial services, national healthcare services, and Big Four consulting before entering public service. Dr. Brian holds a Bachelor’s degree in Forensic Accounting, a Master’s in Information Security Management, and a PhD in Information Technology, Security and Assurance. As well as research and publication on Disaster Recovery, Dr. Brian holds certifications in Cloud Security and Privacy. He is a founding member of the Coalition of City CISOs. The group is dedicated to bringing municipal leaders and cybersecurity professionals together to advance municipal cybersecurity. Dr. Brian and his family reside in the DFW area with their six children. He and his wife actively foster children from the region in hopes to provide them a better start. Over the past seven years they have fostered over 20 kids of all ages from infant to teenagers. In addition, Dr. Brian helps with the Dallas ISD P-TECH program and actively assists with guidance for students around the IT Security field.

Tokio Marine HCC
Brad Breau is the Group CIO for TMHCC with over 26 years of experience in the area of Information Technology. Prior to joining TMHCC, Brad served as Chief Technology Officer and Global Head of Information Technology Operations at AIG Consumer Insurance. His information technology services experience across various industries also includes roles at JPMorgan Chase and Accenture. Brad is married to Tammy Breau for 31 years with 2 daughters, Madison Brown (married to Blake Brown) and Reagan Breau (wedding planned for April 7, 2024)

University Health
William “Bill” Phillips, Jr. serves as Executive Vice President/Chief Information Officer for University Health in San Antonio, Texas. He provides direction and over- sight for the organization’s Information Services Division; including cybersecurity, system operations, applications, strategy, planning and integration for University Hospital and the University Health network of outpatient locations across Bexar County. In 2021, he was named Executive of the Year for the Health Care Hero by the San Antonio Business Journal.

Magellan Midstream Partner
Bhupesh is the CIO for Magellan Midstream Partners, who recently merged with ONEOK. He has multi-sector, multi-nation experience across automotive, labeling and packaging, and consulting. Bhupesh is originally from Los Angeles. He enjoys playing multiple sports and spending time with family.

SRS Real Estate Partners
Alberto Flores is a University of Texas at Austin graduate, originally from Dallas, Texas, with over 15 years of experience in the Commercial and Residential Real Estate industries. His true professional passion lies in process enhancement, honed through Lean Six Sigma methodologies. This expertise allows him to streamline operations, reduce waste, and enhance efficiency in the real estate industry. Beyond his career, he is an enthusiastic cyclist who channels his passion for a greater purpose, raising funds for special causes like the American Diabetes Association. Outside of work and charitable activities, Alberto cherishes quality time with his wife and two dogs. Together, they embrace the “weekend rancher” lifestyle in the Texas hill country, enjoying the serenity and beauty of the countryside whenever they can.

Palantir
Al is currently a senior executive with Palantir Technologies. In his prior role he was the Executive Vice President, Chief Information Officer and Chief Services Officer for a division of NEOM, a Giga project in the Kingdom of Saudi Arabia. He’s also served as a Global & High Technology Enterprise Senior Executive Partner with Gartner’s Advisory Services, COO of a media & advertising company, and multiple other leadership positions.

Chief Technology Officer
Robert Kim, Chief Technology Officer at Presidio advises clients on how to accelerate digital transformation and use technology to drive organizational outcomes. He evaluates IT trends and clients’ specific challenges with the goal of optimizing key business processes to improve end-user experiences, accelerate innovation and create market differentiation. Prior to joining Presidio in 2016, Rob held leadership positions at technology management and consulting firms, with roles in sales engineering, business development, operational excellence, and financial management. He graduated from Penn State with a Bachelor’s Science and earned his MBA at Drexel University.

Sales VP, West
David Belavitch, Vice President of Sales, West. With 25 years experience in the technology sales field, David leads the Presidio Named sales team across the Western 13. David and his team are committed to delivering solutions that foster long-term partnerships. Prior to joining Presidio in 2018, he served as VP of the West at Dimension Data and served as VP West Sales at Nexus IS. David holds a Bachelor of Arts from the University of New Hampshire.

Field CISO, Client Advisor
Dave Trader has been in CyberSecurity for over 20 years now. Dave began his career as a United States Marine serving in both OIF (Operation Iraqi Freedom) and OEF (Operation Enduring Freedom) where Dave specialized in encryption as a Signals Intelligence and Communications expert. Dave is certified in over 70 different areas of CyberSecurity; most notably CISSP, CISM, and as an Ethical Hacker. Dave has an MBA with a specialty in Information Technology and a Bachelor’s Degree in Criminal Justice. Dave is most recently a graduate of the FBI CISO Academy out of Quantico, VA. Dave also serves on the University of Detroit NSA Center of Excellence CyberSecurity Advisory Board and is a coach for the USAF Cyber Patriot Program.
Prior to joining Presidio, Dave was a CISO for seven years at a technology company out of Detroit. Dave specializes in high-security environments, Incident Response, SOC Operations, and security architecture and has been a preferred cybersecurity consultant to Fortune 100 companies for securing their environments for many years. Today, Dave is the Field CISO for Presidio helping countless customers in every vertical with their cybersecurity concerns. Dave thoroughly enjoys the variety of advisory and consulting services.

Sales VP SLED West
Cyndi Barrera, Vice President of Sales for SLED West has nearly three decades of industry experience, and is a seasoned professional known for her leadership and expertise. Her career has been defined by a strong focus on the public sector, particularly in the state/local government and education segments. Cyndi attended Arizona State University, where she studied Organizational Leadership. Prior to joining Presidio in 2020, she held key sales leadership positions at Logical is and Nexus/Dimension Data, where she honed her skills and made a significant impact in the industry.

Chief Innovation Officer
Chris Cagnazzi is the Chief Innovation officer at Presidio leading the Cloud practice, Engineering and Managed Services Operations. He joined Presidio in February of 2012, following the acquisition of BlueWater Communications Group, LLC, where he was the Chief Innovation Officer. In addition, he has served as the VP of Finance of Dimension Data North America and CFO for Integrated Systems Group.

Chief Executive Officer
Bob Cagnazzi is the Chief Executive Officer of Presidio leading the global company in solving clients’ technology challenges. Prior to joining Presidio in 2012, he served as Chief Executive Officer and founder of BlueWater Communications LLC from 2006 until it was acquired by Presidio. Previously, Bob served as Chief Executive Officer of North America at Dimension Data Holdings PLC and led Integrated Systems Group. He holds a Bachelor of Science from St. John’s University and MBA from NYU Stern School of Business.

Senior Vice President, Europe & APAC
Brid Graham is the Senior Vice President of Presidio Europe & APAC. Brid is responsible for driving Presidio’s IT Services, Solutions Business and IT Procurement Business including the company’s Apple Practice. Her teams design and implement innovative solutions that support business transformation, enabling clients to scale in Europe, Middle East and Africa and Asia Pacific. Brid joined the company in 2001 as an Account Manager at Arkphire and has since then has held a variety of leadership roles

Senior Vice President of Sales, Southeast
Michael Kelly is the Senior Vice President of Sales, Southeast at Presidio. He is passionate about the growth and development of his team and the success of Presidio’s customers. Prior to joining Presidio in 2015, Michael spent 11 years at EMC within its Commercial Sales Division building and leading one of the highest revenue producing commercial sales teams in the country. Michael holds a bachelors of science in business from Northeastern University
Senior Vice President, Solutions & Services
Kevin Watkins is Presidio’s Senior Vice President of Solutions and Services responsible for Presidio’s US Professional Services business. He has extensive experience leading client-centric teams and helping organizations adopt technology to gain competitive advantage. Prior to joining Presidio in 2006, Kevin held leadership positions at several consulting and systems integration firms, with roles in sales engineering, business development, operational leadership, and financial management. He holds a bachelors of Business Administration degree in Computer Science and Finance from Temple University’s Fox School of Business

Chief Human Resources Officer
Jenn Jackson joined Presidio in early 2016 as Chief Human Resources Officer and is responsible for all Human Resources strategies and programs including employee engagement and relations, talent acquisition, development and retention, Diversity, Equity & Inclusion, Benefits & Total Rewards, M&A HR due diligence and integration, HR operations and systems, policy, and payroll.
Jenn has over 20 years of HR experience designing and leading HR teams in both public and private global organizations. Prior to coming to Presidio, Jenn was head of Strategic HR and Diversity & Inclusion at Canon U.S.A., Inc. and prior to that she led various Corporate HR functions and M&A due diligence for CA Technologies, Inc.
Jenn was born and raised on Long Island, NY which is where she resides today and was named a New York Business Journal’s Women of Influence 2018.

Chief Financial Officer
Manny Korakis, Chief Financial Officer at Presidio, is responsible for leading the company’s finance team in continuous process improvement and driving profitable growth. Prior to joining Presidio in 2022, Manny was Chief Accounting Officer, Corporate Controller and Corporate Treasurer at IQVIA where he was responsible for global accounting, external financial reporting, financial shared services, capital markets, treasury operations, internal control and financial systems. In addition, he held senior-level positions at American Express Global Business Travel as Corporate Controller and Chief Accounting Officer. Manny spent the majority of his career at S&P Global, where, in his last two years with the company, he was Chief Financial Officer of S&P Dow Jones Indices, a subsidiary with $1 billion in revenue.

Vice President of Sales, Central Region
Justin Filia, Vice President of Sales, Central Region, is a sales leader with over thirteen years of sales management experience and 21 years of IT Industry experience. He is focused on partnering with clients to deliver impactful business outcomes and building, developing, and leading a top-performing sales team. Before joining Presidio in 2020, Justin held senior-level leadership roles at Trace3, VMware, and EMC. He has a bachelor’s degree from the University of Cincinnati.

Vice President, Delivery & Operations
Gopi Pandurangan, Vice President of Delivery & Operations leads Presidio’s team in India in solving customer challenges and delivering strategic cloud-native solutions across all practices. He has more than 25 years of experience in managing and delivering large-scale, complex digital business initiatives with a focus on Data, Web, Mobility and Cloud. Gopi was one of the core foundational team members of Coda Global which Presidio acquired in 2020. His prior experience includes senior-level roles at ESPN leading Sports Data Platforms and international projects that increased efficiency and performance.

Chief Information Officer
Steven Palmese leads Presidio’s internal technology operations and Managed Services teams. He has a wealth of experience in delivering process improvements and innovations in internal IT, infrastructure and applications engineering. Prior to joining Presidio in 2016, Steven held a variety of leadership roles at CA Technologies, most recently as SVP of Engineering.

Chief Legal Officer & General Counsel
Elliot Brecher has served as Chief Legal Officer & General Counsel of Presidio since July 2015. Prior to Presidio, he was General Counsel of Amber Road, Inc., a New York Stock Exchange listed provider of cloud-based global trade management solutions, from 2013. Elliot served as Senior Vice President and General Counsel of Insight Communications Company, Inc., a Midwest-based cable operator, from 2000 until its sale to Time Warner Cable, Inc. in 2012. From 1994 until joining Insight, he was associated with the law firm Cooperman Levitt Winikoff Lester & Newman, P.C., where he became a partner in 1996. Prior to that, Elliot was associated with the law firm Rosenman & Colin LLP.

Barbara Robidoux joined Presidio in 2020 and is responsible for Marketing strategy and execution. She has over 25 years of experience across a range of marketing leadership roles. Barbara joined Presidio from Dell/EMC, where she was Senior Vice President of Marketing for Services. Prior to that, Barbara ran Product Marketing at EMC.

President & Chief Operating Officer
David Hart, President and Chief Operating Officer of Presidio is responsible for sales and technology strategy and execution, emerging businesses development, alliances and sourcing, internal IT and our leasing arm – Presidio Technology Capital. He has served on the advisory boards of several world class technology innovators such as Cisco, Dell Technologies, Palo Alto Networks and Intel. Prior to his current role, Dave served as Chief Technology Officer. He joined Presidio in 2005 when the company acquired Networked Information Systems (NIS), a high growth IT systems integrator, where he led engineering, professional and managed services from its founding in 2000. Prior to NIS, Dave was Vice President of Engineering at Aztec Technology Partners (Nasdaq: AZTC) and at its predecessor, Bay State Computer Group. He holds a BS in Industrial Technology and a MS in Manufacturing Engineering from the University of Massachusetts Lowell.

Senior Vice President, Strategic Business Development
Chris Barney joined Presidio in April of 2018, following the acquisition of Red Sky Solutions, where he served as Chief Executive Officer, and developed the overall company vision and strategy for growth. Chris has more than 25 years of experience in IT engineering, high-tech sales, business development and organizational leadership. Prior to Red Sky, Chris held various executive engineering and sales positions with companies like Entex Information Services, Foundry Networks, and Brocade Systems. Chris enjoys interacting with his clients, prospects, and stakeholders and counts many as friends. He lives in Salt Lake City, UT with his wife and has a son and daughter.

Chief Revenue Officer
John Hanlon joined Presidio in 2020. He has more than 25 years of industry and international experience in information management software, hardware and service. John came to Presidio from Dell/EMC, where he was SVP of Commercial Data Center Sales. He joined EMC in August 2000 and held leadership roles including Vice President, Network Attached Storage Unit; Senior Vice President, Mid-Market Sales; and President, EMC Americas Sales and Customer Operations. Prior to Dell/EMC, John was VP of Sales (Americas) for Parametric Technology Corporation. He also served for 7 years as an Officer in the United States Navy.

Chief Information Security Officer
Greg Hedrick joined Presidio in 2020 as Chief Information Security Officer. Greg has over 25 years’ experience in Cyber Security. Prior to joining Presidio, Greg served as CISO for Purdue University and was responsible for policy and compliance, identity management and security teams including the Security Operations Center for the entire Purdue System.
Greg also collaborated with the State of Indiana to build the Indiana Cyber Security Center. Greg is CISSP and CRISC certified and has served on multiple organizational boards and committees including past President of the Indianapolis Information Systems Security Association, Board of Directors for the Information Systems Audit and Control Association (Indianapolis chapter), and the Educause Security Professionals Conference program committee.

Senior Director, Diversity, Equity, Inclusion & Employee Engagement
Courtney Washington, Presidio’s Chief Diversity Officer, joined Presidio in January of 2016 leading Learning & Development for Presidio. Courtney is responsible for Presidio’s Diversity, Equity & Inclusion strategy and corporate Learning & Development. Prior to Presidio, Courtney has over 10 years of experience in diversity, equity & inclusion, learning & development, talent management, employee engagement, organizational development, and technology/business development.

Executive Vice President & Chief Financial Officer
Christine Komola joined Presidio in 2020 as Executive Vice President, Chief Financial Officer. Prior to joining Presidio, Christine was Executive Vice President and Chief Financial Officer of Covetrus, Inc., a $4 billion global animal health technology and services company. She also enjoyed a 21-year career with Staples, where she was most recently Executive Vice President, Chief Financial Officer from 2012 to 2018. Christine currently serves on three non-profit boards and is a member of the American Institute of Certified Public Accountants.
Chief Technology Officer
Vinu Thomas has served as Chief Technology Officer of Presidio since early 2016. He is responsible for guiding Presidio’s technology strategy, solution and services offerings and industry thought leadership. In addition, Vinu is also responsible for marketing, vendor and product management.
Vinu has built Presidio’s technology teams around networking, mobility, data center and collaboration, while also working on strategic initiatives and investments that include cloud, cyber security, data analytics and virtual desktop infrastructure.
Vinu sits on a number of advisory boards of companies like Cisco, Dell, Palo Alto Networks, Nutanix and VMWARE. Vinu is an advisory board member at Rutgers University where he serves at the Center of Innovation Education.
He was previously Vice President of Solutions for Presidio’s Tristate Area and has a total of 20 years of experience in systems integration, practice building and engineering. Prior to Presidio, Vinu led the Engineering organization for Bluewater Communications Group until it was acquired by Presidio in 2012.
Vice President, Diversity, Equity, & Inclusion
Juliette Austin joined Presidio in 2020 as Vice President of Diversity Equity and Inclusion. Juliette’s focus includes driving systemic actions to ensure Presidio’s commitment in creating an inclusive and equitable environment at all levels.
| Cookie | Duration | Description |
|---|---|---|
| _GRECAPTCHA | 5 months 27 days | This cookie is set by Google. In addition to certain standard Google cookies, reCAPTCHA sets a necessary cookie (_GRECAPTCHA) when executed for the purpose of providing its risk analysis. |
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other". |
| cookielawinfo-checkbox-advertisement | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Advertisement" category. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| bcookie | 2 years | LinkedIn sets this cookie from LinkedIn share buttons and ad tags to recognize browser ID. |
| lang | session | This cookie is used to store the language preferences of a user to serve up content in that stored language the next time user visit the website. |
| lidc | 1 day | LinkedIn sets the lidc cookie to facilitate data center selection. |
| Zoominfo | session | Zoominfo uses technologies to collect and store information when you interact with services it offer to their partners, such as advertising services or analytics. All of those processes are meant to improve your user experience and the overall quality of our services. |
| Cookie | Duration | Description |
|---|---|---|
| _ga | 2 years | The _ga cookie, installed by Google Analytics, calculates visitor, session and campaign data and also keeps track of site usage for the site's analytics report. The cookie stores information anonymously and assigns a randomly generated number to recognize unique visitors. |
| _gat_gtag_UA_111355416_1 | 1 minute | Set by Google to distinguish users. |
| _gid | 1 day | Installed by Google Analytics, _gid cookie stores information on how visitors use a website, while also creating an analytics report of the website's performance. Some of the data that are collected include the number of visitors, their source, and the pages they visit anonymously. |
| _hjAbsoluteSessionInProgress | 30 minutes | This cookie is used to detect the first pageview session of a user. This is a True/False flag set by the cookie. |
| _hjFirstSeen | 30 minutes | This is set by Hotjar to identify a new user’s first session. It stores a true/false value, indicating whether this was the first time Hotjar saw this user. It is used by Recording filters to identify new user sessions. |
| _hjid | 1 year | This is a Hotjar cookie that is set when the customer first lands on a page using the Hotjar script. |
| _hjIncludedInPageviewSample | 2 minutes | This cookie is set to let Hotjar know whether the user is included in the data sampling defined by site's pageview limit. |
| _hjIncludedInSessionSample | 2 minutes | This cookie is set to let Hotjar know whether the user is included in the data sampling defined by site's daily session limit. |
| _hjTLDTest | session | Hotjar test cookie to check the most generic cookie path it should use, instead of the page hostname. This is done so that cookies can be shared across subdomains (where applicable). To determine this, we store the _hjTLDTest cookie for different URL substring alternatives until it fails. After this check, the cookie is removed. |
| oktgid | 1 year | This cookie is used for storing the visitor ID of the user who clicked on an okt.to link. |
| oktsid | session | This cookie is used for storing the session ID of the user who clicked on an okt.to link. |
| Cookie | Duration | Description |
|---|---|---|
| bscookie | 2 years | This cookie is a browser ID cookie set by Linked share Buttons and ad tags. |
| personalization_id | 2 years | Twitter sets this cookie to integrate and share features for social media and also store information about how the user uses the website, for tracking and targeting. |
| VISITOR_INFO1_LIVE | 5 months 27 days | A cookie set by YouTube to measure bandwidth that determines whether the user gets the new or old player interface. |
| YSC | session | YSC cookie is set by YouTube and is used to track the views of embedded videos on YouTube pages. |
| Cookie | Duration | Description |
|---|---|---|
| __gwtCookieCheck | session | This cookie is used to check if the visitors' browser supports cookies. |
| AnalyticsSyncHistory | 1 month | These cookies are used to deliver advertisements more relevant to you and your interests. They are also used to limit the number of times you see an advertisement as well as help measure the effectiveness of the advertising campaign. They remember that you have visited a website and this information is shared with other organizations such as advertisers. |
| li_gc | 2 years | These cookies are used to deliver advertisements more relevant to you and your interests. They are also used to limit the number of times you see an advertisement as well as help measure the effectiveness of the advertising campaign. They remember that you have visited a website and this information is shared with other organizations such as advertisers. |
| UserMatchHistory | 1 month | LinkedIn - Used to track visitors on multiple websites, in order to present relevant advertisement based on the visitor's preferences. |